 Basic Firewall Concepts |
 Basic Firewall Concepts |
Some statistics may help to set the tone for understanding the issues associated with firewalls:
The typical computer placed on the Internet today receives hundreds of remote exploit attempts per day.
According to a Lloyds underwriter, by the early 1990s 4% of the GNP of most industrialized nations was lost to computer crime.
Computer crime losses to large companies in the range of $100M to $500M are fairly common.
The number of attacks against Internet computers has been doubling every 6 months for several years.
According to the American Society for Industrial Security (ASIS) surveys, certain industries are at greater risk, attacks are on the increase, and most companies are successfully attacked more than once per year. Also, 80% of losses due to attacks involve an insider.
According to recent FBI/CSI studies, 95% of businesses have reported losses from computer crime and many of them had breakins through their firewalls.
The approach that seems to be most successful in understanding firewall issues is to look at them as one part of an overall protection strategy. They are technical safeguards whose suitability can only be properly understood in the context of the overall protection program. Other critical protection areas include protection management, policy, standards and procedures, audit, documentation, incident response, testing, physical protection, personnel issues, legal considerations, training ans awareness, educational levels, and organizational structure.
Firewalls are instruments of policy. The policy dictates the purpose of the firewall, what is permitted and prohibited, who controls the decision process and operation, who and when audits and testing take place, cost/benefit tradeoffs associated with the firewall, standards and processes used, and so forth. As a critical starting point, policy issues should be established before firewall implementation, but in reality, firewalls are typically implemented first, leading to policy crises that lead to new policies and new firewalls.
Firewalls are only technical safeguards. They cannot control user behavior or prevent the introduction of other entry points. They have to br properly managed, configured, and tested in order to be effective, and a skilled operator is far more important than a better firewall system. Firewalls cannot understand content, although in some cases they may be able to filter some aspects of content. They cannot make value judgement, but only carry our orders. They are susceptible to subversion. They don't protect against most insider attacks, and these constitute 80% of losses due to computer related crime. They rarely deal effectively with denial of services or corruption-based attacks, are not always transparent and automatic, and typically run on top of insecure operating systems. In other words, firewalls are one tool in the toolbox of effective protection, but they are not the end all of security solutions.
Firewalls are not plug-and-play solutions to anything. They require a lot of work to set up properly and operate over time, they are very easy to set up incorrectly, and they are hard to properly maintain over time. They need to be adapted to changing needs in most environments, each service has to be managed and watched, and audit records need to be examined to see what is going on. Configuration chages have to be tested, and most often, changes induce errors that don't show up for some time. Firewalls are different in each organization to meet its policies and conditions, and to fit into the overall organizational protection plan.
Firewalls are typically the interface between two or more parts of the information environment. When they are the interface to the outside world, they represent your organization, and must reflect what you want the world to see of you. Are they the only interface? Should they be? Are there legal notice requirements associated with use? The role of the firewall is tightly linked to public relations as well as technical protection.
Most firewalls create a protective barrier, which can be thought of as an egg shell. It is a thin outer shell typically protecting a gooey center. 80% of losses from attacks involve insiders, and they operate predominantly in the gooey center.
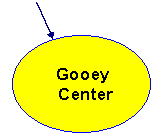
An example will help to drive this home. In one demonstration for a multi-billion dollar company, a red team member was successful in extracting more than $1M within a few days. There was a very sophisticated firewall in place, but in a few days unlimited internal network access was obtained, accounts were obtained on several computers, new expense accounts were created, and lot more. The method used was 'perception management'. The attacker talked a secretary into providing a cryptogrpahic modem and the proper keys necessary to gain remote access through the firewall. In another similar example, expected losses were estimated at more than $1B after one week of red teaming effort. These attacks were not sophisticated or complex, and they succeeded in bypassing firewalls that were technically speaking very strong.
Firewalls are typically only the 'front gate' of your security system. But attackers tend to seek the path of least resistence. You need to watch out for back doors into your system, such as dial-in modems, wiring that goes outside of your physical control, and software that can be introduced when sent in the mail.
In the early days of firewalls, routers were used for this function because of their natural fit as a connectivity point between networks and because of their role in controlling traffic flows.

Routers already limited traffic flow. This is done to facilitate efficient communication, to control local connectivity, to restrict access, ro make IP-based decisions on addresses and ports, and in some cases to handle IP option fields.
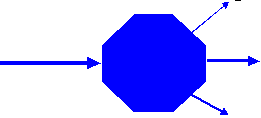
Routers become packet filters. As initial firewalls, to limit internal traffic. To restrict access to select networks. To limit TCP traffic. To limit file transfers. To prevent NIS service. Finer grain packet filters.

One way to think of and picture network firewalls is like physical firewalls. When there is a fire on the Internet, it may be cooler inside the firewall than on the other side. But at the same time, an open window or a lit match can set a fire inside. The goal of the firewall is to make it cooler inside for a period of time, and just like a physical firewall, no computer will resist raging outside attack forever.

Typically, firewalls are used between the Internet and yout network, between parts of an organization that need to be protected from each other, on private links between organizations, between national boundaries, in places where information flow should be restricted, or wherever a control point is desired.
It is important to understand that the physical analogy is very limited because (1) fire, unlike human actors, is not intelligent or malicious in the same way as people are, (2) in the case of fire, we are only trying to keep it away, while in the case of information we want some of it to come in and some of it to go out, and (3) we can often tell when there is a fire by obvious means, but we are often unaware when we are under information attack.
These are basic principles...
The minimum software principle:
| Redundancy improves integrity:
|
Conclusion: Only use the software you need to have.
The principle of least privilege:
|
| |
Principal: "That which is not explicitly premitted is denied" - Bellovin and Cheswick
Putting your eggs in one basket:
Firewalls don't eliminate the need for host security.
Firewalls can be thought of as filters. In this role, they can (1) block large classes of packets, provide different responses in different directions, provide different filters for different interfaces, selectively pass different packets in diffferent directions, and make more complex decisions, like; (1) State-dependent decisions, (2) sequenced responses, (3) Increased response modes, (4) Partial service shutdowns, (5) Service restoration.
Firewalls also support - and in some instances provide - 'DMZ' functions. In this case the 'DeMilitarized Zone' is used for servers that need to cross the boundary between internal and external access. For example, e-mail servers must forward email in both directions, Web services must be updated from inside the firewall and in some cases support back-end databases that are entirely within the enterprise, encryption services are often used to create virtual private networks that span firewall boundaries, and deception and incident response systems are often incorporated within DMZs.
Firewalls act as filters between different areas and support other protective functions of the enterprise that uses them. Less software, more well thought out software, redundancy, and control over privileges all provide for stronger firewall functions.