 Linux Firewalls |
 Linux Firewalls |
Application gateway is a hole designed for an application to pass through. The intent is to prevent undesired applications, but the 'hole' may be imperfect. May not provide all desired services, may provide undesired services, may allow tunnelling of services, may let application-level attacks through.
Proxy server acts as surrogate for a real server. It takes a request from a client, translates addresses and ports for internal use, makes the request of the server and gets an answer, translates the answer back for the client, and sends the packet back out.
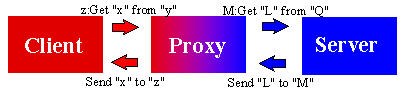
How a proxy works: Maintain a translation table, convert (parse and create) incoming packets to outgoing packets, don't forward original packets, only provide select services. Limits attacks to provided services, eliminates direct contact, eliminates OS weaknesses not associated with the allowed services.

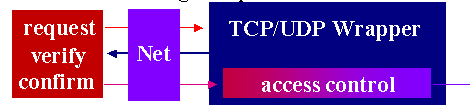
Wrappers check incoming requests for source and destination, verify properties such as validity of DNS name, source routing disabled, etc., do access control based on criteria, log events, pass information on to application(s), and require no change to the operating system.
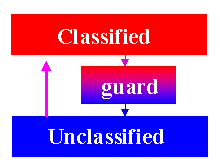
Special services such as mail guards, content controls, emai lencryption, special authenticators (challenge/response, time or use), multi-level secure gateways, route controllers and diversifiers, and so forth.
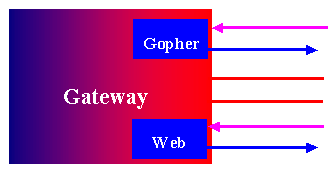
Secure servers like the secure get-only web server on the Whiote Glove, secure gopher server, etc. offer proven security properties and can be trusted in some cases to operate directly on a gateway.
Gateways are hard to configure and maintain properly, sometimes have problems with new protocols, open up some holes in protocols such as SMB, etc., limit bandwodth, failure denies services, weakness opens up the whole network.
Gateway security is an issue because gateway computers are gneral purpose computers that can be attacked if thay have insecurities. Defense-in-depth helps (wrappers, ipchains, secure services, proxies, NAT), special gateway security helps (Read-Only...), special care helps, rapid response helps.
Gateway limits: Bandwidth limited, non-constant group delay, increased packet delay, resource exhaustion often feasible, DoS severe, Gatewar corruption can be very bad, all services must be managed
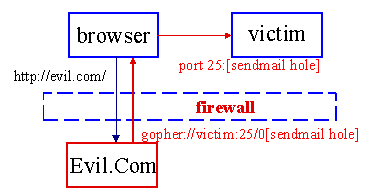
Can your firewall stop this?
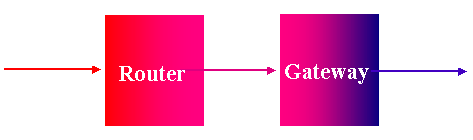
One router - can limit IP pairs, services, SYNACK stuff - may have source routing limits, IP frag ,imitsm does not prevent app level attacks, does not prevent IP add forgery, may provide built-in encryption

One gateway - could be perfect but most are not - hard to manage right - susceptible to config errors

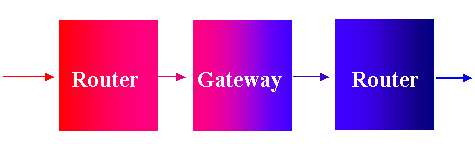
One router one gateway (fewer config errors, good for simple networks)
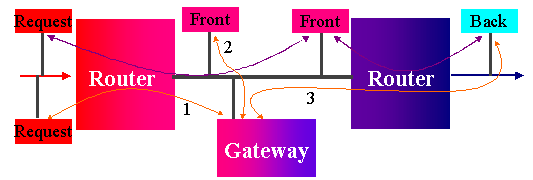
Router Gateway Router
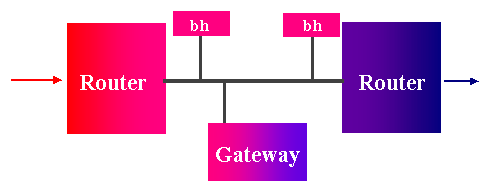
Bastion host and DMZ.
Front end back end
Summary chart:
| Router | Gateway | R&G | R&G&R&more | |
|---|---|---|---|---|
| manage | easy | very hard | hard | hard |
| policy | simple | hard | hard | hard |
| procedures | simple | very hard | hard | hard |
| documents | simple | very hard | hard | hard |
| audit | simple | very hard | hard | hard |
| testing | simple | very hard | hard | hard |
| cost | low | high | hard | high |
| effective | poor | variable | moderate | high |