 Information Resource Guide |
 Information Resource Guide |
Computer viruses are programs which replicate themselves, attach themselves to other programs, and perform unsolicited and often malicious actions. Self-replication is the key trait that distinguishes viruses from other destructive programs. For instance, a Trojan Horse is a program which performs unsolicited actions, but it cannot replicate and spread on its own.
Viruses are destructive to productivity as well as data. An example of productivity damage is the Stoned virus which simply writes "Your computer is stoned" on the screen. Data damage is exemplified by the Hare virus (popularized in Summer 1996), which erases data from hard drives. In any case, viruses always cause some degradation of system resources, and some degree of wasted time for computer users. Since they are unsolicited and concealed, it does not seem accurate to call any virus "benign."
Critical to a virus' "success" is the ability to remain undetected for a long enough period to replicate and spread to new hosts. By the time the virus' presence is revealed, through unusual computer "behavior," damage to data or taunting messages, it usually will have been quite some time since the original infection took place.
This delay in time, between infection and manifestation, obviously makes it more difficult to trace the origin of the virus and/or the route it took to reach one's system. So delays are often made an inherent "feature" within a virus' design. A virus may monitor for a trigger event, which is a computer condition that, when it occurs, will cause the virus' payload to be delivered.
Examples of trigger events include dates (such as March 6 for the infamous Michelangelo virus), times, number of file saves or disk accesses, or file sizes. Specific keystroke sequences, in any predictable combination, can also be triggers.
A payload is an action performed by a virus - usually, but not always, the action that reveals the virus' presence. Examples of payloads include:
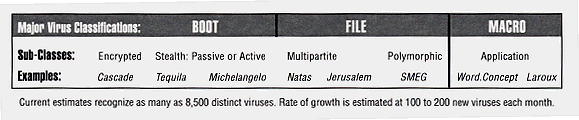
Before the inception and rapid proliferation of the Macro category, most IBM-compatible and Macintosh viruses fell into two basic categories: Boot, such as "Michelangelo" and File, such as "Jerusalem."
Boot viruses activate upon system start-up and are more common. They infect a system's floppy or hard disk and then spread (by replicating and attaching) to any logical disks available. File viruses are actually programs which must be executed in order to become active, and include executable files such as .com, .exe and .dll. Once executed, file viruses replicate and attach to other executable files. Since most viruses attach at the beginning or end of processes, their execution goes unnoticed.
7.1.1 Additional Virus Classifications
Other troublesome general virus sub-classes that are active today include Stealth (active and passive), Multipartite, Encrypted, Polymorphic, and Macro.
Stealth viruses (such as "Tequila") are difficult to detect because, as their name implies, they actually disguise their actions. Passive Stealth viruses can increase a file's size, yet present the appearance of the original file size, thus evading Integrity Checking - one of the most fundamental detection tactics.
Active Stealth viruses may be written so that they actually attack installed anti-virus software (generic or brand-specific), rendering the product's detection tools useless.
Multipartite viruses, such as "Natas," have the characteristics of both boot and file viruses. "Cascade" is a well-known Encrypted virus. The challenge of Encrypted viruses is not primarily one of detection, per se. The encryption engine of this type of virus masks its viral code – making identification, as opposed to detection, more difficult.
The Polymorphic category ("SMEG" is an example) has grown considerably, presenting a particular detection challenge. Each polymorphic virus has a built-in mutation engine. This engine creates random changes to the virus' signature on given replications. Therefore, detection and prevention of recurring infections further requires frequent anti-virus component updates from a given vendor.
7.2 The New Macro Virus Threat
If you send or receive documents or spreadsheets, chances are your computer has been or will be infected at one time or another by a macro virus. Relatively new on the computing scene, these computer viruses are spreading faster than most anti-virus software makers can find ways to detect and remove them. Macro viruses are now the most prevalent computer viruses in the world, largely due to the new way in which they spread--they attach themselves to word processor and spreadsheet documents, which often are transmitted as e-mail attachments via the Internet throughout the world.
This new means of virus proliferation calls for new methods of virus detection. One such approach is based on intelligent, rule-based scanning -- a technique that searches for and removes even macro viruses never before analyzed. This approach combines the following elements:
Despite a significant increase in the usage of anti-virus products, the rate of computer virus infection in corporate America has nearly tripled in the past year, according to a survey released in April 1997 by the International Computer Security Association (ICSA), formerly the National Computer Security Association. Virtually all medium and large organizations in North America experienced at least one computer virus infection firsthand, and the survey indicated that about 40 percent of all computers used in the surveyed companies would experience a virus infection within a year.
Macro viruses, which unlike their predecessors, are carried in common word processing documents and spreadsheets, are the biggest problem, representing 80% of all infections. Moreover, the instances of macro virus infection doubled about every four months in 1996. This makes these viruses the fastest to spread in the history of the ICSA.
The Number One macro virus encountered in the survey, by far, was the Concept virus, also known as prank macro, wm-Concept, winword.Concept, wordmacro.Concept, ww6, and ww6macro. Within months of its discovery in the fall of 1995, the Concept virus accounted for more than three times the number of virus encounters reported for the previous leader, the "Form virus." Today, the Concept virus has infected almost one-half of all ICSA survey sites (see Figure 1).
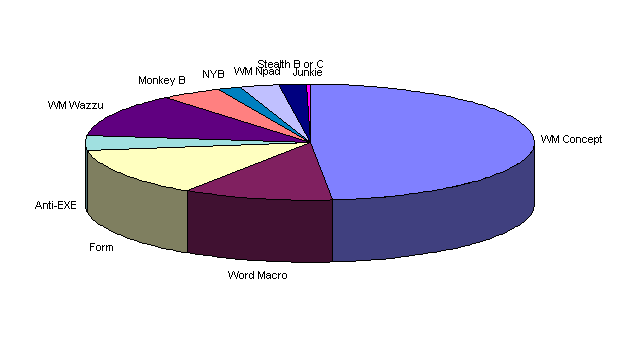
Figure 1. The Concept virus and other Word macro viruses were the dominant viruses encountered in 1997, according to a virus prevalence survey conducted by the International Computer Security Association.
Perhaps even more worrying than the meteoric rise in infections by this particular virus is what it bodes for the future. Microsoft Word™, Microsoft Excel™, and other document and spreadsheet files were once thought to be immune to infection. Since these virus carriers are now the most prevalent types of files exchanged in the world, the threat of viruses has evolved in a big way. With the exponential growth of the Internet for e-mail and file exchange, macro viruses now represent the most widespread virus threat ever.
"Macro viruses are incredibly successful viruses," says Eva Chen, CTO of Trend Micro. "Because they hitchhike on document and spreadsheet files, they can travel both on floppy diskettes and across computer networks as attachments to electronic mail. Then they spread quickly by taking advantage of e-mail, groupware, and Internet traffic."
Adding to growing concern about these viruses is the ease of their creation. Prior to the macro virus era, creating a virus required some knowledge of assembly language or other complex programming language. Today, almost anyone can write a macro virus using Visual Basic, which uses English-like commands (see Figure 2). There is even a guided step-by-step template for creating Word macro viruses available on the Internet.
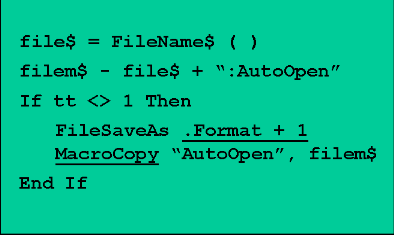 Figure
2. Macro viruses written in visual basic are easier to write than their
assembly language predecessors.
Figure
2. Macro viruses written in visual basic are easier to write than their
assembly language predecessors.
While most of the more than 500 macro viruses known at the time of this writing are not destructive, many cause a considerable loss of productivity and staff time. Average financial cost per ‘virus disaster,’ according to the ICSA, rose to $8366 in 1997, and Figure 3 shows that virus incident costs are shifting from predominantly low levels to intermediate levels. Concept restricts file saving operations, and other macro viruses have been known to manipulate information, control data storage, and even reformat hard drives. This potential destructiveness has system administrators buzzing about how to address this new threat.
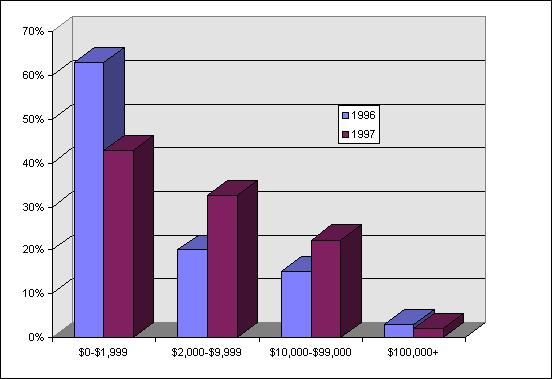
Figure 3. According to the ICSA 1997 Computer Virus Prevalence Survey, the stated costs of virus incidents tended to shift from less than $2000 to the range of $2000-$99,000 [1].
7.2.1 Macro Viruses: How They Work
Understanding how to protect against macro viruses requires some knowledge about what makes these viruses tick. Just when we thought we understood how viruses work--by attaching executable code to other executable code in software--along come viruses that attach themselves to document files and spreadsheets. How do macro viruses pull this off?
The answer is that there is more to today's word processing or spreadsheet file than meets the eye.
Traditional files like these consist solely of text. But today's increasingly sophisticated word processing and spreadsheet files carry macros with them that can provide a variety of features to your documents and spreadsheets. For example, macro commands can perform key tasks, such as saving files every few minutes, or they can prompt you to type in information, such as a name and address into a form letter. These macros, part of the document itself, travel with the file as it is transferred from user to user, either via floppy diskette, file transfer, or e-mail attachment.
Some of these macro commands have special attributes that force them to execute automatically when the user performs various standard operations. For example, Word uses five predefined macros, including the AutoOpen macro, which executes when a user opens a Word document, and AutoClose, which runs when you close the document.
Macro viruses gain access to word processing and spreadsheet files by attaching themselves to the executable portion of the document--in AutoOpen, AutoExec, AutoNew, AutoClose, AutoExit, and other file macros. For example, the Concept virus attaches itself to AutoOpen and FileSaveAs in Word
(See Figure 4).
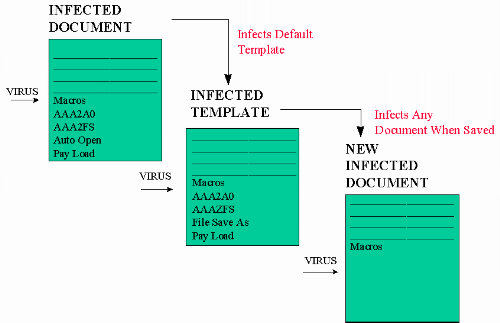
Figure 4. Concept latches onto one macro that is automatically run in Word: AutoOpen. By attaching itself to AutoOpen, the virus takes control as soon as an infected document is opened. Next, it infects the default template. Then, by attaching itself to FileSaveAs, the virus effectively spreads itself to any other document when it is saved.
Macro viruses are particularly difficult to eradicate because they can hide in attachments to old e-mail messages. For example, the administrator of a network infected by a macro virus may take pains to eliminate it. But when an employee returns from a vacation and opens an e-mail attachment with the virus and forwards it to others on the network, the virus can spread again, necessitating a second round of detection and disinfection.
This migration of viruses to word processing and spreadsheet files mirrors user computing patterns. In fact, this parallel evolution of viruses and computing media has been going on for years. When the primary means of exchanging files was the floppy diskette, the most prevalent viruses were boot sector infectors, which resided on the first sector of a diskette. Later, the wide use of internal networks built around file servers allowed viruses to spread by modifying executable files. Today, the ICSA reports that commonly exchanged word processed and spreadsheet files sent over the Internet as e-mail attachments are the most common carrier of viruses [1].
The increase in virus incidence despite rising anti-virus usage can lead to but one conclusion. "It is obvious that existing virus protection software isn't working," says Chen. "Traditional methods have not been successful in combating viruses entering networks from new entry points--e-mail and the
Internet." Hence, the Concept virus seems to be aptly named, since dealing with it and viruses like it reliably and effectively requires new concepts in virus detection.
The traditional approach to virus detection has been to gather samples of suspicious code, conduct analysis, create new virus signature files, and distribute them to customers.
Assuming that users periodically download updates of anti-virus software, this approach works well for viruses that do not spread quickly and for viruses without large numbers of variants. Many anti-virus software packages that take this approach use pattern-matching algorithms to search for a string of code that signals malicious actions. When virus writers began to foil this "fingerprint analysis" by encrypting their code, anti-virus software developers responded by using the decryption routine included with the virus, emulating operation of the code in an isolated environment, and determining if the code was malicious.
Unfortunately, the Concept virus and other macro viruses often elude these techniques for several reasons. The ease with which these viruses can be developed, coupled with the vast number of word processing and spreadsheet documents exchanged throughout the world every day via the Internet, is leading to the rapid proliferation of many variants of each macro virus. Essentially, macro viruses are spreading and mutating so fast that anti-virus software designed to detect and remove them is obsolete soon after it is shipped to users.
Stopping Macro Viruses Requires New Approaches
The solution is to supplement pattern matching with a more sophisticated technique--analyzing the behavior of each macro and determining whether the macro's execution would lead to malicious acts.
This enables detection and cleaning of even those macro viruses that have not yet been captured and analyzed. But implementing this approach is not easy, requiring intelligent, rule-based scanning.
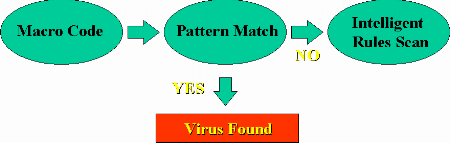 A
rule-based scanning engine should complement pattern matching with algorithms
to examine macro commands embedded in word processed and spreadsheet files
and identify malicious code. This type of solution should also instantly
detects and cleans known and unknown macro viruses, eliminating the time-consuming
steps that traditional virus approaches require (see Figure 5).
A
rule-based scanning engine should complement pattern matching with algorithms
to examine macro commands embedded in word processed and spreadsheet files
and identify malicious code. This type of solution should also instantly
detects and cleans known and unknown macro viruses, eliminating the time-consuming
steps that traditional virus approaches require (see Figure 5).
Figure 5. A new approach to stopping macro viruses detects and removes even previously unknown macro viruses from word processed and spreadsheet files.
To efficiently extract only the macro portion of each word processed or spreadsheet file it examines, this new approach is based on OLE2 (object linking and embedding) technology. Files such as those created in Word are also based on OLE2 structure, which organizes each file into discreet components (e.g., document and objects).
This new approach examines the document portion of the file only to identify key information about the macros that accompany the document, such as the locations of the macros (i.e., which "object" locations contain macros, as expressed in the macro table). The anti-virus technology does not scan the (sometimes very long) text portion of the file, since this portion cannot contain viruses. In addition to maintaining high-speed scanning performance, this approach reduces the likelihood of false positive virus indications -- possible when large text files are scanned.
After extracting the macro code, this approach compares it with patterns from known viruses. If a match is found, the user is alerted. Otherwise, the anti-virus software applies a comprehensive set of intelligent binary rules that can detect the presence of almost all macro viruses. For example, if the macro code indicates it would reformat a hard drive without prompting the user for approval to do so, the user would be alerted of the virus. This is one part of several sets of such checks that are performed. Since some macro viruses are activated when files are simply opened, virus detection is performed on files before they are even opened by any application.
Macro Virus Dependencies:
Application Popularity- The more common and "horizontal" the application, the greater the risk. More specialized or vertical market-specific programs aren't attractive enough to offer a large "breeding ground" for macro viruses.
 Macro
Language Depth- The extent of the application's macro language affects
a virus writer's ability to create a successful macro virus. Macro Implementation-
Not all programs embed macro commands into data files. For instance, AmiPro
documents will not necessarily contain "invisible" macro information. The
easier it is to transfer and execute the macro from within the application,
the faster the spread of the virus.
Macro
Language Depth- The extent of the application's macro language affects
a virus writer's ability to create a successful macro virus. Macro Implementation-
Not all programs embed macro commands into data files. For instance, AmiPro
documents will not necessarily contain "invisible" macro information. The
easier it is to transfer and execute the macro from within the application,
the faster the spread of the virus.
Viruses Are Often Blamed for Non-Virus Problems
As awareness of computer viruses has grown, so has the tendency to blame "some kind of virus" for any and every type of computing problem.
In fact, more cases of "not a virus" are encountered by customer support staff at anti-virus vendors than are actual virus infections, and not only with inexperienced users. Typical symptoms of viral infection such as unusual messages, screen color changes, missing files, slow operation, and disk access or space problems may all be attributable to non-virus problems.
Possible culprits include lost CMOS data due to a faulty system battery, another user's misuse, fragmented hard disks, reboot corruption, or even a practical joke. For instance, some PCs play the Happy Birthday song through their speakers every November 13. Sounds like a virus payload, but it happens only in computers containing BIOS chips from a certain batch that was sabotaged by a former programmer at the BIOS vendor. Switching out the BIOS chip eliminates the annual singing message.
Even deliberately written unwelcome programs are not always viruses...
As stated before, a multitude of hardware and software incompatibilities and/or bugs may cause virus-like symptoms, but there is also the in-between world of destructive, deliberately designed programs which still are not viruses. Again, it is important to remember that the key distinction of viruses is their ability to replicate and spread without further action by their perpetrators. Some non-virus programs are more destructive than many actual viruses.
Non-virus threats to user systems include Worms, Trojan Horses and Logic Bombs. In addition to the potential for damage these programs can bring by themselves, all three types can also be used as vehicles for virus program propagation.
Network worm programs use network connections to spread from system to system, thus network worms attack systems that are linked via communications lines. Once active within a system, a network worm can behave as a computer virus, or it could implant Trojan horse programs or perform any number of disruptive or destructive actions. In a sense, network worms are like computer viruses with the ability to infect other systems as well as other programs. Some people use the term virus to include both cases.
To replicate themselves, network worms use some sort of network vehicle, depending on the type of network and systems. Examples of network vehicles include:
A network worm exhibits the same characteristics as a computer virus: a replication mechanism, possibly an activation mechanism, and an objective. The replication mechanism generally performs the following functions:
The activation mechanism might use a time bomb or logic bomb or any number of variations to activate itself. Its objective, like all malicious software, is whatever the author has designed into it. Some network worms have been designed for a useful purpose, such as to perform general "house-cleaning" on networked systems, or to use extra machine cycles on each networked system to perform large amounts of computations not practical on one system. A network worm with a harmful objective could perform a wide range of destructive functions, such as deleting files on each affected computer, or by implanting Trojan horse programs or computer viruses.
Two examples of actual network worms are presented here. The first involved a Trojan horse program that displayed a Christmas tree and a message of good cheer (this happened during the Christmas season). When a user executed this program, it examined network information files, which listed the other personal computers that could receive mail from this user. The program then mailed itself to those systems. Users who received this message were invited to run the Christmas tree program themselves, which they did. The network worm thus continued to spread to other systems until the network was nearly saturated with traffic. The network worm did not cause any destructive action other than disrupting communications and causing a loss in productivity [BUNZEL88].
The second example concerns the incident whereby a network worm used the collection of networks known as the Internet to spread itself to several thousands of computers located throughout the United States. This worm spread itself automatically, employing somewhat sophisticated techniques for bypassing the systems' security mechanisms. The worm's replication mechanism accessed the systems by using one of three methods:
It was unclear what the network worm's objective was, as it did not destroy information, steal passwords, or plant viruses or Trojan horses. The potential for destruction was very high, as the worm could have contained code to effect many forms of damage, such as to destroy all files on each system.
A Trojan horse program is a useful or apparently useful program or command procedure containing hidden code that, when invoked, performs some unwanted function. An author of a Trojan horse program might first create or gain access to the source code of a useful program that is attractive to other users, and then add code so that the program performs some harmful function in addition to its useful function. A simple example of a Trojan horse program might be a calculator program that performs functions similar to that of a pocket calculator. When a user invokes the program, it appears to be performing calculations and nothing more, however it may also be quietly deleting the user's files, or performing any number of harmful actions. An example of an even simpler Trojan horse program is one that performs only a harmful function, such as a program that does nothing but delete files. However, it may appear to be a useful program by having a name such as CALCULATOR or something similar to promote acceptability.
Trojan horse programs can be used to accomplish functions indirectly that an unauthorized user could not accomplish directly. For example, a user of a multi-user system who wishes to gain access to other users' files could create a Trojan horse program to circumvent the users' file security mechanisms. The Trojan horse program, when run, changes the invoking user's file permissions so that the files are readable by any user. The author could then induce users to run this program by placing it in a common directory and naming it such that users will think the program is a useful utility. After a user runs the program, the author can then access the information in the user’s files, which in this example could be important work or personal information. Affected users may not notice the changes for long periods unless they are very observant.
An example of a Trojan horse program that would be very difficult to detect would be a compiler on a multi-user system that has been modified to insert additional code into certain programs as they are compiled, such as a login program. The code creates a trap door in the login program, which permits the Trojan horse's author to log onto the system using a special password. Whenever the login program is recompiled, the compiler will always insert the trap door code into the program; thus, the Trojan horse code can never be discovered by reading the login program’s source code. For more information on this example, see [THOMPSON84].
Trojan horse programs are introduced into systems in two ways, they are initially planted and unsuspecting users copy and run them. They are planted in software repositories that many people can access such as on personal computer network servers, publicly accessible directories in a multi-user environment, and software bulletin boards. Users are then essentially duped into copying Trojan horse programs to their own systems or directories. If a Trojan horse program performs a useful function and causes no immediate or obvious damage, a user may continue to spread it by sharing the program with other friends and co-workers. The compiler that copies hidden code to a login program might be an example of a deliberately planted Trojan horse that could be planted by an authorized user of a system, such as a user assigned to maintain compilers and software tools.
Logic Bombs are a favored device for disgruntled employees who wish to harm their company after they have left its employ. Triggered by a timing device, logic bombs can be highly destructive. The "timer" might be a specific date (i.e., the logic bomb that uses Michelangelo's birthday date to launch "his" virus embedded within). An event can also be the designed-in trigger (such as after the perpetrator's name is deleted from a company's payroll records).
Computer viruses, like Trojan horses, are programs that contain hidden code, which performs some usually unwanted function. Whereas the hidden code in a Trojan horse program has been deliberately placed by the program's author, the hidden code in a computer virus program has been added by another program, that program itself being a computer virus or Trojan horse. Thus, computer viruses are programs that copy their hidden code to other programs, thereby infecting them. Once infected, a program may continue to infect even more programs. In due time, a computer could be completely overrun as the viruses spread in a geometric manner.
An example illustrating how a computer virus works might be an operating system program for a personal computer, in which an infected version of the operating system exists on a diskette that contains an attractive game. For the game to operate, the diskette must be used to boot the computer, regardless of whether the computer contains a hard disk with its own copy of the (uninfected) operating system program. When the computer is booted using the diskette, the infected program is loaded into memory and begins to run. It immediately searches for other copies of the operating system program, and finds one on the hard disk. It then copies its hidden code to the program on the hard disk. This happens so quickly that the user may not notice the slight delay before his game is run. Later, when the computer is booted using the hard disk, the newly infected version of the operating system will be loaded into memory. It will in turn look for copies to infect. However, it may also perform any number of very destructive actions, such as deleting or scrambling all the files on the disk.
A computer virus exhibits three characteristics: a replication mechanism, an activation mechanism, and an objective.
The replication mechanism performs the following functions:
the same.
The activation mechanism checks for the occurrence of some event. When the event occurs, the computer virus executes its objective, which is generally some unwanted, harmful action. If the activation mechanism checks for a specific date or time before executing its objective, it is said to contain a time bomb. If it checks for a certain action, such as if an infected program has been executed a preset number of times, it is said to contain a logic bomb. There may be any number of variations, or there may be no activation mechanism other than the initial execution of the infected program.
As mentioned, the objective is usually some unwanted, possibly destructive event. Previous examples of computer viruses have varied widely in their objectives, with some causing irritating but harmless displays to appear, whereas others have erased or modified files or caused system hardware to behave differently. Generally, the objective consists of whatever actions the author has designed into the virus.
As with Trojan horse programs, computer viruses can be introduced into systems deliberately and by unsuspecting users. For example, a Trojan horse program whose purpose is to infect other programs could be planted on a software bulletin board that permits users to upload and download programs. When a user downloads the program and then executes it, the program proceeds to infect other programs in the user's system. If the computer virus hides itself well, the user may continue to spread it by copying the infected program to other disks, by backing it up, and by sharing it with other users. Other examples of how computer viruses are introduced include situations where authorized users of systems deliberately plant viruses, often with a time bomb mechanism. The virus may then activate itself at some later point in time, perhaps when the user is not logged onto the system or perhaps after the user has left the organization.
Without control of the "human element" and proper implementation, anti-virus software alone cannot provide full protection.
However, it is still the critical element in the fight against viruses. As stated before, non-virus problems may appear to be virus related, even to sophisticated users. Without anti-virus software, there is no conclusive way to rule out viruses as the source of such problems and then arrive at solutions.
Effective anti-virus software must be capable of performing three main tasks: Virus Detection, Virus Removal (File Cleaning) and Preventive Protection. Of course, detection is the primary task ad the anti-virus software industry has developed a number of different detection methods, as follows.
Five Major Virus Detection Methods:
Today, all effective products leverage a combination of detection methods because of the large number of virus types and their many tricks for invasion and disguise. Anti-virus software is a constantly evolving field, and as the knowledge base deepens, vendors can further refine these methods and develop even more effective future solutions.
7.4 Anti-Virus Policies and Considerations
The best anti-virus software in the world cannot protect you if it is not deployed systematically throughout the enterprise (even if "the enterprise" is a single home-based computer!).
Many people think they can dismiss a disk, shared or e-mailed file because it came from someone they know and trust. What they aren't considering is that their friend colleague, customer or vendor is working on another system, with its own set of vulnerabilities from different outside conditions.
Computer users must recognize that
the virus threat is too pervasive today to be ignored by anyone...the number
of users who never come into contact with others' files is small and becoming
smaller every day, especially with the tremendous growth of online services
and Internet usage.
7.4.0 Basic "Safe Computing" Tips
This is because vulnerability to viruses increases in proportion to the number of machines, the extent of their interconnection, and the number of non-technical users who may view anti-virus vigilance as "someone else's job." (In contrast, a solo entrepreneur is likely to take the virus threat seriously because he or she will have to deal with infection results personally or pay an outside consultant.)
All organizations are different in the way they operate and the industries they serve, so no one anti-virus scheme is correct for all enterprises. However, at the very least, a company's program should include ongoing user education and a system for tracking virus activity (suspect and real) in addition to using anti-virus software.
Ultimately, your goal is to provide consistent, effective protection and a "damage control and recovery" plan for virus infections that may occur despite your efforts. In addition, and perhaps most importantly, you want to achieve this while minimizing any negative impact on staff productivity and system/network resources.
Therefore, to formulate a comprehensive anti-virus plan, it is necessary to first analyze the "bit picture" of your organization along with its more detailed computing characteristics.
5 Key Factors in Anti-Virus Program Planning
The more PCs you have, or the
higher the ratio of computers to people, the more you need a formalized,
thoroughly documented anti-virus program.
"Interconnection" does not necessarily
mean electronically networked. If data is frequently moved from one PC
to another via diskettes or other media, those computers are effectively
connected, whether they are separated by a few yards or many miles. Again,
the frequency of data interchange may be as important as the methods of
transfer.
Assuming that multiple locations
are involved because they are linked via data communications, more locations
will require more coordination and reporting between the various IT staffs,
as well as more user training.
Every organization has an inherent
pace of operations, mostly dependent on the nature of its business. No
matter how "busy" it is, a research laboratory's pace will not be as fast
as that of a securities brokerage firm. In general, the faster the pace
of operations, the greater the risk of virus infection because of the faster
rate at which new data is being generated and distributed. faster pace
= more frequent new data = greater risk !
Whatever the profile of your organization's computing characteristics and virus vulnerability, it is important to remember that anti-virus measures must be balanced in relation to the actual functions of various machines and their users.
Even within a specific location of the enterprise, there may be computers for which you need to sacrifice some level of anti-virus security in order to maintain necessary throughput and/or productivity. Cost is another factor that must be balanced against "ideal" protection levels, for all equipment and personnel in the organization.
7.4.1 Anti-Virus Implementation Questions
7.4.2 More Virus Prevention Tips
The larger your network, and/or the more sensitive your enterprise's data security position, the more you should seek guidance from industry peers and the anti-virus software industry before finalizing your plan.
Representatives from the leading vendors have experience in providing anti-virus solutions for many different kinds of distributed environments, in many different industries. Plus, their training programs and consulting services can be invaluable, helping to prevent both costly virus incidents and ensuring that your program is more cost-effective.
7.4.3 Evaluating Anti-Virus Vendors
Although anti-virus software companies design their products to detect and remove viruses, there is more to making a smart choice than comparing detection rates and/or product prices.
The fact that anti-virus software is necessary for everyone in the enterprise means that it must work alongside a variety of applications, and probably on multiple computing platforms within the location. Therefore, a common anti-virus product that can work "seamlessly" throughout the enterprise is desirable, for both cost-effectiveness and simpler administration.
The software must also be effective against the majority of common and damaging viruses, yet be as unobtrusive to productivity as possible. (Bear in mind that this is as important for user compliance as for the bottom line - if users feel hampered by anti-virus procedures they may "overlook" them in their haste to get work done.)
Another major factor to consider is the burgeoning number of viruses - as many as 200 new ones each month. Anti-virus software that does not include regular updates cannot provide adequate protection for long.
To ensure that you are providing the best possible solution, the anti-virus vendor you ultimately choose should satisfy the following primary criteria:
Section References
7.1 NAI White Paper. "Current Computer Virus Threats, Countermeasures and Strategic Solutions".1997
7.2 Landry, Linda, Trapping the World's Most Prevalent Viruses. Trend Micro, Inc. 1998
"Roll-Your-Own Macro Virus," Virus Bulletin, September, 1996, p. 15.
Joe Wells, "Concept: Understanding the Virus and Its Impact," Trend Micro, Incorporated.
"ICSA 1997 Computer Virus Prevalence Survey, ICSA.
7.3.0 Wack, John P and Carnahan, Lisa J. Computer Viruses and Related Threats:A Management Guide. NIST Special Publication 500-166. U.S Dept of Commerce
DENNING88 Denning, Peter J.; Computer Viruses; American Scientist, Vol 76, May-June, 1988.
DENNING89 Denning, Peter J.; The Internet Worm; American Scientist, Vol 77, March-April, 1989.
FIPS73 Federal Information Processing Standards Publication 73, Guidelines for Security of Computer Applications; National Bureau of Standards, June, 1980.
FIPS112 Federal Information Processing Standards Publication 112, Password Usage; National Bureau of Standards, May, 1985.
MACAFEE89 McAfee, John; The Virus Cure; Datamation, Feb 15, 1989.
NBS120 NBS Special Publication 500-120; Security of Personal Computer Systems: A Management Guide; National Bureau of Standards, Jan 1985.
SPAFFORD88 Spafford, Eugene H.; The Internet Worm Program: An Analysis; Purdue Technical Report CSD-TR-823, Nov 28, 1988.
THOMPSON84 Thompson, Ken; Reflections on Trusting Trust (Deliberate Software Bugs); Communications of the ACM, Vol 27, Aug 1984.
DENNING88 Denning, Peter J.; Computer Viruses; American Scientist, Vol 76, May-June, 1988.
DENNING89 Denning, Peter J.; The Internet Worm; American Scientist, Vol 77, March-April, 1989.
FIPS73 Federal Information Processing Standards Publication 73, Guidelines for Security of Computer Applications; National Bureau of Standards, June, 1980.
FIPS112 Federal Information Processing Standards Publication 112, Password Usage; National Bureau of Standards, May, 1985.
MACAFEE89 McAfee, John; The Virus Cure; Datamation, Feb 15, 1989.
NBS120 NBS Special Publication 500-120; Security of Personal Computer Systems: A Management Guide; National Bureau of Standards, Jan 1985.
SPAFFORD88 Spafford, Eugene H.; The Internet Worm Program: An Analysis; Purdue Technical Report CSD-TR-823, Nov 28, 1988.
THOMPSON84 Thompson, Ken; Reflections on Trusting Trust (Deliberate Software Bugs); Communications of the ACM, Vol 27, Aug 1984.
7.3.3 Wack, John P and Carnahan, Lisa J. Computer Viruses and Related Threats:A Management Guide. NIST Special Publication 500-166. U.S Dept of Commerce
DENNING88 Denning, Peter J.; Computer Viruses; American Scientist, Vol 76, May-June, 1988.
DENNING89 Denning, Peter J.; The Internet Worm; American Scientist, Vol 77, March-April, 1989.
FIPS73 Federal Information Processing Standards Publication 73, Guidelines for Security of Computer Applications; National Bureau of Standards, June, 1980.
FIPS112 Federal Information Processing Standards Publication 112, Password Usage; National Bureau of Standards, May, 1985.
MACAFEE89 McAfee, John; The Virus Cure; Datamation, Feb 15, 1989.
NBS120 NBS Special Publication 500-120; Security of Personal Computer Systems: A Management Guide; National Bureau of Standards, Jan 1985.
SPAFFORD88 Spafford, Eugene H.; The Internet Worm Program: An Analysis; Purdue Technical Report CSD-TR-823, Nov 28, 1988.
THOMPSON84 Thompson, Ken; Reflections on Trusting Trust (Deliberate Software Bugs); Communications of the ACM, Vol 27, Aug 1984.
7.4 NAI White Paper. "Current Computer
Virus Threats, Countermeasures and Strategic Solutions".1997