 Information Resource Guide |
 Information Resource Guide |
8.0 Virtual Private Networks: Introduction
8.1 Making Sense of Virtual Private Networks
The VPN market is on the verge of explosive growth. A virtual private network (VPN) broadly defined, is a temporary, secure connection over a public network, usually the Internet. Though the term is relatively new, everyone from the telcos, to operating system vendors, to firewall suppliers and router companies has rushed to offer some type of VPN capability. Why? Because VPNs make sense, and as a result, the market is expected to reach at least several billion dollars by the year 2001.
By leveraging the Internet, VPNs offer significant cost savings, greater flexibility, and easier management relative to traditional internetworking methods, such as leased lines and dial-up remote access.
However, choosing an appropriate solution from the recent flood of VPN offerings can be a difficult task for information technology managers who have no spare time. Each solution presents varying levels of security, performance, and usability, and each has its benefits and drawbacks.
Though a catch-all Internet security solution sounds appealing, there is currently no product that can equally address the different aspects of securing online communication. As a result, the VPN market has begun to stratify according to corporate demands for tighter security, better performance, and effortless usability and management. To select an appropriate product, IT managers should be able to define their corporation's particular business needs. For instance, does the company only need to connect a few trustworthy remote employees to corporate headquarters, or does the company hope to create a secure communications channel for its branch offices, partners, suppliers, customers, and remote employees?
At minimum, a VPN should encrypt data over a dynamic connection on a public network to protect the information from being revealed if intercepted. Beyond that basic function, VPN features customarily include tools for authentication, and a limited number provide integrated access control and authorization capabilities. In addition to enumerating the possible VPN components, this white paper outlines the predominate VPN technologies and interprets the nuances of different VPN approaches so IS professionals can better decide how to secure their corporate communication.
8.2 Defining the Different Aspects of Virtual Private Networking
Before online business can truly reach its potential, corporations must feel comfortable using the Internet as the backbone for secure communication. VPNs are the first real step toward that end. When implemented correctly, they protect networks from viruses, snoops, corporate spies, and any other known threat that results from mistakes in configuration, poorly implemented access controls, lack of system management, weak authentication, and "back-door" entry points to the network.
Sample VPN Requirements to Consider
Security
including key sizes 40, 56, and 128 and ciphers RC4, DES, and Triple DES?
including viruses, file types, Java and Active X, and protocols such as FTP, Telnet, etc.?
control according to parameters such as type of authentication, type of encryption, user identity, time of day, source address, destination address, and type of application?
network traffic?
notify an administrator of specific events? |
Interoperability
with perimeter security, such as a firewall or router?
other protocols such as IPv4, IPSec, and PPTP/L2TP?
authentication and encryption standards?
application types?
cross-platform environment, including all Windows and UNIX operating systems?
Netware, RADIUS, and ACE databases?
methods of load balancing? |
Ease-of-Use
for the desktop? Is the client transparent to the end-user?
sign-on, or does the user have to log on each time an application is launched?
support hundreds of thousands of users?
management of the security system?
and UNIX operating systems? |
The three fundamental features that define virtual private networking are encryption, authentication, and access control. While strong authentication and encryption are critical components of the VPN, they are relatively simple to deploy and verify. Access control, on the other hand, is relatively complex because its deployment is tied intimately to every other security tool. Roughly speaking, the security of a VPN is a function of how tightly authentication, encryption, and access control are connected. If one component is lacking, the VPN will be lacking.
Where a company might use a guarded gate in the physical world to block all unauthorized visitors, a firewall might be used in the analogous VPN world. Until recently, that's as far as the comparison could be drawn, because in the VPN world there hasn't been a way to provide varying levels of access. Now, with emerging VPN technologies and solutions, companies can verify someone's identity with strong authentication technologies like token cards, digital certificates, or even fingerprints. Once identified, users are granted access to resources according to very detailed profiles based on identity and often a user's role within a larger group. VPNs are also beginning to provide tools to monitor a user's activity once inside the corporate network.
Prior to even connecting to the Internet, corporations should develop a security policy that clearly identifies who can have access to what resources, leaving room for growth and change. And before implementing a VPN, corporations should evaluate their current security paradigm to determine what equipment can be leveraged for a VPN. Once the budget has been decided on, companies should consider all of the benefits they hope to derive from a VPN, such as increased profits through streamlined processes, improved customer service from providing more personalized information faster, and stronger strategic relationships from the easy and secure exchange of information.
A comprehensive solution might incorporate a firewall, router, proxy server, VPN software or hardware, or all of the above. Any one of those pieces might sufficiently secure communication, depending on a company's priorities, but it's more likely that a combination of tools will provide the most comprehensive solution.
IS professionals can effectively use VPNs to address three predominant internetworking scenarios:
Intranets are defined here as semi-permanent WAN connections over a public network to a branch office. These types of LAN-to-LAN connections are assumed to carry the least security risk because corporations generally trust their branch offices and view them as an extension of the corporate network.
In this case, the corporation generally controls both the source and destination nodes. IS administrators should ask whether or not this assumption holds true for their company.
General Case
When the two endpoints of a data channel are relatively trusted, a company can comfortably opt for a VPN solution that focuses on performance over security, which is limited to the strength of the encryption and authentication methods between the two routers. High volumes of data are often exchanged between LANs on an intranet VPN, so the premium is wisely placed on speed and smooth interoperability. The LANs that are connected by centralized corporate databases or other enterprise-wide computing resources should appear to be part of the same corporate network. Many of the firewall, router, and frame relay vendors, as well as some of the ISPs, are offering solutions that adequately secure intranet VPNs while transferring data quickly and reliably.
Highly Secure Case
Security threats often come from within an organization. In fact, according to a study issued jointly by the FBI and the Computer Security Institute, almost half of all computer break-ins occur within a company.
If a company is concerned about proprietary information being leaked by employees, whether intentionally or accidentally, or if a company routinely applies different levels of trust to branch offices or individuals, then it should consider investing in a VPN solution that can control the information flow on an authenticated, user-specific policy level rather than on a trusted subnet basis. IT managers should look closely at solutions that provide reasonable ways to implement and manage these advanced role-based policies.
Corporations are just now beginning to realize the advantages the Internet offers over traditional direct dial-up remote access. Many corporations, burdened by the effort of maintaining large modem pools and the expense associated with long distance charges, are finding that using the Internet as a backbone for remote access is much more affordable and easier to implement and maintain than traditional solutions.
In any remote access VPN scenarrio, usability is an importan criterion. Most security flaws are attributed to configuration errors, so the easier the system is to manage, the less likely is the chance for oversight. On the client side, simplicity is critical because many traveling employees and telecommuters either lack the technical proficiency or the access to technical resources for troubleshooting. Clients should not have to manually build a VPN tunnel, "manually" meaning having to launch VPN software each time the user wants to establish a secure communication channel. Instead, the VPN software should launch automatically at start-up and run transparently in the background. On the server side, centralized and easy management is essential because monitoring large numbers of users and adding and removing users on a regular basis can quickly become chaotic and can create a security risk.
General Case
With most remote access VPNs, it is assumed that a corporation trusts the person at the other end of the link, which is typically a traveling or remote salesperson. Rather than worrying that the employee might do damage to the network or steal proprietary information, the company is probably more concerned with the unknown element between the two end points. These companies will generally assume a "transparent access" policy, best described as: "The remote employee should have unfettered access to all resources that would be available to them if they were sitting at their desk at corporate headquarters."
The priority, therefore, becomes encrypting the data in transit so that only the intended recipient can decipher it. Most VPNs can meet this basic security requirement, so evaluators should consider additional criteria, such as the strength of the encryption cipher and the authentication method for providing additional security.
Highly Secure Case
The industries that are the most leery of any kind of security risk, such as the financial, health, and government sectors, are paradoxically the earliest adopters of VPN technologies, which have the perception of being less secure than traditional means of networking. In reality, the best VPN technologies are much more secure than most leased lines and dial-up remote access, because highly secure VPNs encrypt all data and generally provide very detailed user profiles for access control.
Highly secure remote access solutions are deployed by sophisticated IT shops with a strong understanding of the security risks inherent in any network communication. These shops generally adopt a "controlled access" policy for their remote users. This is best described by the following policy statement: "The remote employee should have tightly controlled access to specific resources on the network according to the requirements of their job function."
These companies deploy policy-driven VPNs to provide highly secure remote access over the public networks. Secure policy-driven VPNs authenticate individual users, not just IP addresses, so that a corporation knows which employee is trying to gain access to the network. This can be accomplished through common passwords digital certificates, token cards, smart cards, or biometrics, such as fingerprint or iris scanning. Once an employee has authenticated to the corporate VPN server, he or she is granted a certain level of access depending on his or her profile, which is usually set up by a network administrator to match the corporate security policy and enforced by a sophisticated system of datastream filters and access control parameters. This three-tier system is essential for companies that allow their employees to access mission-critical information, particularly when those employees are not entirely trusted.
Any time a company wants to provide varying levels of access so that different resources can be made available to different employees when appropriate, or when a company wants to prevent "back-door" holes into the network, which is common in some systems, then a more robust VPN solution is recommended. In other words, a highly secure VPN should be able to intercept network traffic destined for a particular host, add the required encryption, identify individual users, and apply restrictions and filter content accordingly.
Unlike intranets that are relatively isolated, extranets are intended to reach partners, customers, and suppliers, as well as remote employees. Securing that wide area network requires diligence and the right tools. An extranet VPN needs to be able to provide a hierarchy of security, with access to the most sensitive data being nested under the tightest security control. It should secure all applications, including TCP and UDP applications, such as Real Audio, FTP, etc.; corporate vertical applications, such as SAP, BAAN, PeopleSoft, Oracle, etc.; and "homegrown" applications, such as Java, Active X, Visual Basic, etc. Because most corporate computing environments are heterogeneous with many legacy systems, a sound VPN solution should be extremely versatile and interoperable with multiple platforms, protocols, and authentication and encryption methods.
General vs. Highly Secure Case
The main objective of an extranet or business-to-business VPN is to ensure that mission-critical data arrive intact and in the proper hands without ever exposing protected resources to potential threats, so companies should only consider implementing the most secure breed of VPNs.
The security elements of a VPN can be prioritized differently, but with an extranet VPN, all the fundamental pieces 3/4 encryption, authentication, and access control 3/4 should be integrated tightly with some type of perimeter security. Usually this means a company will place a VPN proxy server behind an impenetrable firewall that blocks all unauthenticated traffic. Any traffic that is allowed in is then funneled through a common portal directly to the VPN server, which filters traffic according to company policy. It is essential for the connection between the firewall and the VPN to be strong and reliable, and the client software should be as transparent as possible.
The most secure VPNs are built around a "directed" architecture, as opposed to a bi-directional "tunneled" method. Directed VPNs transmit encrypted information at a higher level in the networking protocol stack than tunneled VPNs, and security and control increase as functionality moves up the network hierarchy. Directed VPNs act as proxy servers, which means they do not open any direct connections into corporate networks, preventing IP addresses from being "spoofed," or mapped. Tunneling hides information in IP packets at the packet level, exposing them more easily to attack. Because all data is proxied in directed VPNs, administrators can tell at a glance who has been trying to gain access to the network and how often.
Unlike tunneled VPNs, directed VPNs protect connected networks from each other’s security flaws. Directed VPNs do not assume a two-way trusted relationship between connecting parties. If security is breached in the directed model, only the attacked network is exposed, not the linked networks. In the tunneled model, when one network is attacked, each successive network is susceptible to the same attacker. In the directed model, each company's IS managers can set their own access privileges and be confident they are not exposing their networks to unknown security problems.
Tunneled VPNs, as the name implies, open tunnels within the Internet and secure information traveling through them with basic packet filtering. This approach gives participating companies weakly secured access to each other's networks, with no way to fine-tune access control. These types of solutions often mistakenly start with the faulty assumption that there should be peer-to-peer trust among companies connected by VPNs. When trading partners or customers are involved, that is rarely the reality.
When companies conduct multi-faceted business transactions over public networks, simple encrypted tunnels will not suffice. Online business, or electronic commerce, is not restricted to credit card transactions. It involves complex negotiations and collaboration on projects. When vital, confidential information is involved, IS professionals cannot risk compromising any portion of the network. An extranet VPN should use the highest encryption available, which is currently 128 bits, except when restricted by exportation laws. In addition, the VPN should support multiple authentication and encryption methods since business partners, suppliers, and customers are likely to have varying network infrastructures and platforms.
In a true business-to-business scenario, IS managers should look for a VPN that filters access to resources based on as many parameters as possible, including source, destination, application usage, type of encryption and authentication used, and individual, group, and subnet identity. Administrators should be able to identify individual users, not just IP addresses, either through passwords, token cards, smart cards, or any other method of authentication. Passwords are usually sufficient for casual office use, but they are not considered as secure as token or smart cards. Employees are often careless with their passwords, and they rarely change their codes, whereas token and smart cards change the passcode on a regular basis, often as frequently as every 60 seconds.
Once authenticated, administrators should be able to route authorized traffic to protected resources without jeopardizing network security. The access control is what ultimately distinguishes the level of security among VPN solutions. Without being able to control exactly who has access to each resource on a network, a VPN is virtually useless beyond the network's perimeter. Once authenticated, a user should not have carte blanche to the network. Rather, specific permissions should be granted to each user in order to retain the most control over every resource. Security should increase, not lessen, as a user moves inward toward the most sensitive data. By utilizing strong encryption, authentication, and access control methods, all working seamlessly within a VPN solution, companies can seal their corporate networks from almost any security breach.
8.4 Understanding VPN Protocols
The VPN security market is young, and standards are still evolving, but a handful of protocols have emerged as the leading choices for building VPNs. An IS manager should not have to base his or her purchasing decision on the technology used, but understanding the benefits of each protocol may help clarify the related strengths and weaknesses of different VPN end products. Although there are many possible security approaches for creating a VPN, the following protocols show the most promise for lasting in the market, whether for the quality of their design or their financial backing.
SOCKS v5 was originally approved by the IETF as a standard protocol for authenticated firewall traversal, and, when combined with SSL, it provides the foundation for building highly secure VPNs that are compatible with any firewall. It is most appropriately applied to VPNs that require the highest degree of security, since its strength is access control.
SOCKS v5 was developed in 1990 by David Koblas and championed through
the IETF by NEC Systems Laboratory. It is currently the only IETF-approved
standard being used to create VPNs. Though it is not as well known as some
of the other protocols, it has received widespread support from industry
leaders such as Microsoft, Netscape, and IBM. SOCKS v5 is the protocol
used in Aventail’s policy-based VPN solution.
Advantages
SOCKS v5 controls the flow of data at the session, or circuit, layer, which maps approximately to layer five of the OSI networking model. Because of where it functions in the OSI model, SOCKS v5 provides far more detailed access control than protocols operating at the lower layers, which permit or reject packets based solely on source and destination IP addresses. SOCKS v5 establishes a virtual circuit between a client and a host on a session-by-session basis and provides monitoring and strong access control based on user authentication without the need to reconfigure each new application.
Because SOCKS v5 and SSL operate at the session layer, they have the unique ability to interoperate on top of IPv4, IPSec, PPTP, L2TP, or any other lower-layer VPN protocol. In addition, SOCKS v5 and SSL have more information about the applications running above them than do lower-layer protocols, so they can provide very sophisticated methods of securing traffic.
SOCKS v5 stands out as the only VPN approach to use a directed architecture, which essentially protects destination computers by proxying traffic between source and destination computers. When used in conjunction with a firewall, data packets are passed through a single port in the firewall (port 1080 by default) to the proxy server, which then filters what is sent forward to a destination computer. This prevents administrators from having to open multiple holes in their firewall for different applications. For additional security, the VPN proxy server hides the address structure of the network, making it more difficult for confidential data to be cracked. Another design advantage of SOCKS v5 is that the client is non-intrusive. It runs transparently on the user's desktop and does not interfere with networking transport components, as do lower-layer protocols, which often replace the Winsock DLL, TCP/IP stack, and low-level drivers, interfering with desktop applications.
SOCKS v5 is also highly flexible. It works easily with multiple security technologies and platforms, which is critical for IS professionals managing heterogeneous computing environments. It offers modular plug-in support for many authentication, encryption, and key management methods, providing IS managers the freedom to adopt the best technologies for their needs. Plug-and-play capabilities include access control tools, protocol filtering, content filtering, traffic monitoring, reporting, and administration applications. SOCKS v5 can filter data streams and applications, including Java applets and ActiveX controls, according to very detailed specifications.
SOCKS v5 is the only VPN protocol that can interoperate with other VPN protocols, such as PPTP, IPSec, and L2TP, and it is ready for implementation today. Because the SOCKS v5 protocol is designed specifically for highly secure environments, analysts expect that SOCKS v5 and appropriate plug-ins will be used primarily for highly secure remote access and the extension of private client networks across multiple organizational perimeters.
Disadvantages
Because SOCKS v5 adds a layer of security by proxying traffic, its performance generally is slightly slower than that of lower-layer protocols, depending on how the VPN is implemented. Though it is more secure than solutions located at the lower network or transport layers, the extra security requires more sophisticated policy management than at the lower layers. Also, client software is required to build a connection through the firewall to transmit all TCP/IP data through the proxy server.
One of the most widely known VPN security choices is Point-to-Point Tunneling Protocol (PPTP) from Microsoft. It is embedded in Microsoft’s Windows NT v4.0 operating system and is used with Microsoft’s Routing and Remote Access Service. It sits at the datalink layer, which maps approximately to layer two of the OSI model. It encapsulates PPP with IP packets and uses simple packet filters and the Microsoft Domain networking controls to provide access control. PPTP and its successor, L2TP, are seen as tools to extend the current PPP dial-up infrastructure supported by Microsoft, most ISPs, and the remote access hardware vendors.
Layer Two Transport Protocol (L2TP) has evolved from the combination of Microsoft’s PPTP protocol and Cisco Systems' Layer 2 Forwarding (L2F). It supports multiple, simultaneous tunnels for a single client and is targeted at the telco and ISP markets. With L2TP, the end user dials up a local ISP POP without encryption, and the ISP, acting as an agent for the end user, creates an encrypted tunnel back into the secure destination.
PPTP and L2TP have received broad support from the current leaders in the remote access services market, which includes Cisco, Bay Networks, 3Com, Shiva, and Microsoft, because they provide an effective way for these vendors to migrate their current corporate dial-up products to Internet-based methods of building tunnels. Analysts predict that PPTP and L2TP will play a dominant role in the Internet-based remote access market when security requirements are relatively low.
Advantages
IS professionals running Microsoft-centric shops will find PPTP and L2TP ready-made to work with their systems. Because they use packet-filtering that makes use of existing network routers, they are typically less complicated to implement, and they are transparent to end users.
In typical Microsoft fashion, PPTP is free. Microsoft includes it as a component of its RAS and router software, formerly known as Steelhead. When affordability in a Microsoft-only environment is an issue, PPTP is a viable solution. L2TP will likely follow the same path and be included in upcoming versions of NT servers and Windows 32-bit desktop clients.
Most VPNs secure TCP/IP traffic, but PPTP and L2TP support additional networking protocols such as Novell’s IPX, NetBEUI, and AppleTalk. They also support flow control, which keeps traffic from overwhelming clients and servers. They enhance network performance by minimizing dropped packets, thus cutting down on re-transmission.
Disadvantages
PPTP and L2TP are typical tunneled approaches to VPN security, which means they encapsulate non-secure IP packets within secure IP packets. They use IP frames to create an open data passageway between two computer systems. Once a tunnel is open, source and destination identification is no longer required. The tunnel is bi-directional, so while it encrypts data traveling along the Internet, it does not provide a way to monitor or control what gets passed between the two points.
One often overlooked limitation is that PPTP and L2TP are limited to 255 concurrent connections. In addition, end users are required to manually establish a tunnel prior to connecting to the intended resource, which can be a hassle. Also, the selection of authentication and encryption standards is very limited, and currently no strong encryption or authentication is supported.
Another concern is that there are currently no versions of PPTP or L2TP available for older Microsoft operating systems or UNIX. PPTP is still very narrowly targeted for Microsoft-specific networking.
PPTP and L2TP are currently only proposed standards. PPTP is presently supported by Microsoft’s Windows NT 4.0 server, NT workstation, and Windows 95. Remote access vendors, such as Ascend and Shiva, are backing L2TP, and Microsoft plans to incorporate L2TP into Windows NT server version 5.0.
Internet Protocol Security (IPSec) has gained a lot of recent attention in the industry. It evolved from the IPv6 movement, and as a standard promoted by the IETF, IPSec will be a broad-based, open solution for VPN security that will facilitate interoperability between VPNs. IPSec can be configured to run in two distinct modes 3/4 tunnel mode and transport mode. In tunnel mode, IPSec encapsulates IPv4 packets within secure IP frames to secure information from one firewall to another. In transport mode, information is encapsulated in such a way that it can be secured from endpoint to endpoint. In other words, the security wrapper does not obscure the end routing information as it does in the tunnel mode. Tunnel mode is the most secure method for deploying IPSec, but it results in significant overhead on a per-packet basis.
IPSec has had a very slow adoption cycle due primarily to dissension among the various IETF committees over key management standards and other issues. Intranet VPN applications using IPSec should start to be introduced to the market sometime in 1998. Commercial implementations using IPSec are still relatively immature, but the greatest supporters of the standard are the router vendors and the VPN hardware vendors who hope to usurp the router vendors in the market for building intranet (LAN-to-LAN) VPNs. Analysts predict that IPSec will be the primary standard for this segment of the VPN market.
Advantages
IPSec defines a set of standard protocols for authentication, privacy, and data integrity that are transparent to the application and the underlying network infrastructure. Unlike PPTP, IPSec supports a wide variety of encryption algorithms, such as DES, Triple DES, and IDEA. It also checks the integrity of transmitted packets to make sure they have not been tampered with en route.
IPSec was designed to provide security between multiple firewalls and routers, which makes it an optimum solution for LAN-to-LAN VPNs. IPSec's promise is that, because it is a natural extension to IP, it could be applied very broadly to the VPN market, ensuring interoperability among VPNs running over TCP/IP.
Disadvantages
For a number of years now, IPSec has been held out to the Internet community as the way to do secure networking. While IPSec holds great promise and will be a critical standard in IP-based networking, to date many attempts to deploy IPSec have been frustrated by the IETF committee infighting, which has delayed true interoperability between IPSec implementations. IPSec will likely be very successful in the LAN-to-LAN environments, but it will be of limited utility in the client/server configuration over the next few years.
IPSec in the client-to-server configuration has a number of disadvantages that may be difficult to get around. IPSec, for all practical intents, requires a public key infrastructure. Today's PKIs, including Internet Security Association Key Management Protocol (ISAKMP), have achieved relatively limited penetration, and concerns about overall scalability still exist. In addition, IPSec implementations require a known range of IP addresses or fixed IP addresses to establish identity. This makes them impractical to use in dynamic address environments, which are common to Internet service providers.
IPSec does not support network protocols other than TCP/IP. As a standard, it does not specify a methodology for access control other than simple packet filtering. And, because it uses IP addressing as part of its authentication algorithm, it is seen as less secure than some of the higher-layer protocols that identify individual users.
Probably the most significant drawback to IPSec today is Microsoft's lukewarm support of the standard. Microsoft has been noticeably silent about support for IPSec in its client operating systems. Since IPSec in some ways competes with PPTP and L2TP for client tunnel building, it is not clear that Microsoft will make wholesale changes to the core IPv4 stack to support IPSec on the desktop. Regardless, replacing current IP stacks or widespread deployment of new device drivers is seen as extremely expensive and labor intensive.
8.5 Matching the Right Technology to the Goal
Corporations are finding that without Internet connectivity, they cannot compete in their respective markets. The Internet offers immediate access to information, which is tremendously beneficial as long as it is not coupled with security risks. Vendors are offering a number of VPN options to provide the necessary security to make internetworking worthwhile, but no solution today can solve every corporate need for secure communications. Each has its own benefits and drawbacks. Network administrators should carefully consider their priorities and base their decision on matching criteria. While some VPNs are easy to set up, others are more secure. And those that are fast may lack interoperability. The one certainty corporations can count on is an evolving market.
Each corporation has its own business style. Smaller shops may just need to provide their traveling sales representatives with a way to remotely access the corporate network. The larger the organization, the more likely it is to use an intranet to share information among its employees and branch offices. As security is added to VPNs, companies are extending those intranets and implementing full extranets. Considering that VPNs are moving in the direction of secure extranet VPNs, which are basically supersets of remote access and intranet VPNs, network managers should carefully review the scalability and potential of VPN solutions to support future business-to-business transactions over untrusted networks.
In general, the better performing pure VPN solutions will be targeted at the intranet (LAN-to-LAN) and less secure remote access VPN environments, and the more secure policy-based VPNs will be targeted at the extranet (business-to-business) and highly secure remote access VPN environments. VPNs that are implemented at layers two and three of the OSI model should demonstrate better performance than those at higher layers, and VPNs at layer five and above should offer much greater security. With that in mind, the following recommendations reflect the best practices for the different approaches to VPN
implementation.
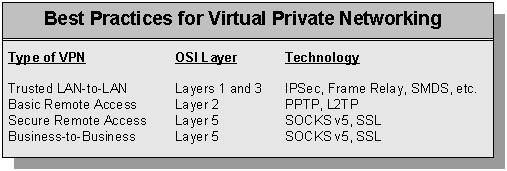
VPNs based on SOCKS v5 are best used by companies that need to provide highly secure, client-to-server connectivity for comprehensive business solutions, such as building a supply-chain extranet or highly secure remote access infrastructure. Because SOCKS v5 is an open standard that sits at the session layer, it can operate apart from lower-level protocols or add value to the VPN tunneling protocols that lack security features like access controls.
IPSec contains the most appropriate functionality to support trusted LAN-to-LAN VPNs. It does not require a client piece of software, so it provides appealing solutions for companies that want to exchange large amounts of data as fast as possible, typically the intranet VPN scenario. Because many of the router and internetworking vendors are building IPSec functionality into their platforms, IPSec will probably be the most important standard for this part of the market.
As mentioned earlier, PPTP and its variant, L2TP, are most appropriately used for remote access VPNs, as long as the limited encryption and authentication seem sufficient, and as long as Windows is the platform used. PPTP and L2TP will more than adequately meet many IT shops' basic remote access requirements.
According to a November 1997 issue
of The Forrester Report, the VPN market is still immature, but early adopters
of VPNs, ranging from start-ups to Fortune 50 companies, have been optimistic.
Forrester predicted that the appeal of VPNs will broaden as security, performance,
and interoperability wrinkles are smoothed out. One Forrester respondent
from an aerospace company summed up a common forecast, saying, "Our VPN
usage will explode over the next two years. Any application we need to
share 3/4 internal Web, database access, personnel data, and benefits 3/4
will run over the network." Whatever solution a corporation decides on,
it should adopt a security framework that can utilize the best of evolving
technologies, function in a heterogeneous corporate environment, and map
real-world trust relationships to the network.
Section References
8.0 "Making Sense of Virtual
Private Networks", Aventail Corporation