Historical Models of Human Cognition and Deception
- "If men define situations as real, they are real in their consequences." -
W.I. Thomas
Our current model of human deception is based on the
combination of Lambert's model of cognitive deception and the notions of
this paper. In this model, the stimulus response behavior of a person
is broken down into sensors, buffer memories, short and long term
memories, a controller, a manager, and affectors. This model of
cognitive components is interpreted by a picture of what those
components do. These are called cognitive processes. The cognitive
processes are shown in the figure below:
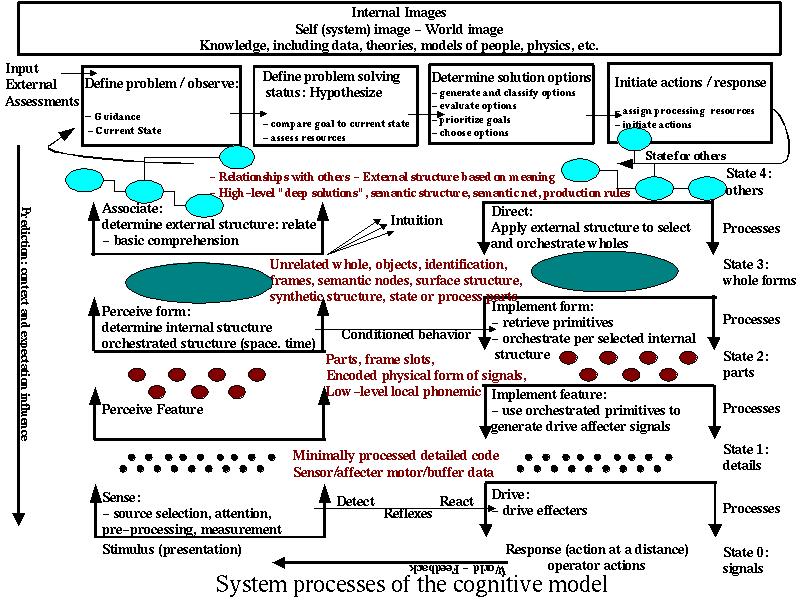
Deception happens when inputs are below thresholds of detectability for any given process (concealment) when they are designed to cause the normal interpretation mechanisms to conclude that something is there when it is not (simulation), or when they are designed to cause erroneous interpretation (a combination of concealment and simulation).
In the case of human deception, parameters of sensory concealment are fairly well known. Many studies have been undertaken to understand the ability of people to hear sounds, see images, feel contacts, smell odors, and taste flavors at different concentrations with and without the presence of noise, as a function of time, and biased by pre-existing conditions. Reaction times have been measured and reflexes cataloged so that if we wish to generate a reflexive response to intentionally generated sensor inputs (simulation) we can often do so with a high degree of certainty. These human traits can be used in combination to carry out various deceptions, such as the use of motion and noise to distract attention for a period of a second or two, with a high degree of certainty against a large portion of the human population and they have been widely exploited in such areas as magic tricks.
Conditioned behaviors have been studied since the time of Pavlov [***] and such behaviors can be intentionally created and used both for offensive and defensive purposes. For example, we can repeatedly create a simulated stimulus followed by a simulated non-threatening follow-on behavior. After some number of repetitions, the stimulus will be largely ignored in anticipation of the conditioned non-threatening follow-on behavior. The simulated stimulus is chosen to be indifferentiable from the stimulus of the real attack which is then concealed from higher cognitive processes for a time because of the prior conditioning created by the training process. An example of a defensive use of conditioned behaviors is conditioning of individual operators of a computer system to respond to particular screen outputs with particular motor movements reflected on their keyboards. For example, we might flash a colored dot on the screen and train a particular operator to press the shift key when it appears. After a short while this becomes a conditioned behavior that is no longer operative at the conscious level and which has no other side effects. It happens quickly and automatically. This behavior can then be used to identify the operator while others observing the process may not even notice the behavior and, if they do, they will likely not be able to invoke in a timely fashion until it becomes a conditioned behavior for them as well. The conditioned behavior is an example of a intentionally created simulation intended to be concealed from the observer who might take over the operator's position in an overrun of the position or try to duplicate the operators actions when the operator is not present.
At 'higher' cognitive levels, deceptions often take the form of misdirections (combinations of concealment and simulation). Typically, these misdirections involve an expectation of some sort which is closely modeled by the deception and only altered in order to carry out the objectives of the deception. For example, when a lonely person meets an individual that seems to be compatible with them, they may have romantic expectations associated with their social context. This will build toward a level of trust over time which will then reduce inhibitions against to such activities as shared use of money. The same pattern appears in almost all frauds by deception. These sorts of deception takes a wide variety of specific forms depending on the time frame required for the deception and the nature of the desired target behaviors, but they share a common bond. They operate by:
(1) simulating a situation matching an expectation
(2) with some deviation that is beyond the momentary ability of the target to rationally analyze.
Whitlock
Chuck Whitlock has built a large part of his career on identifying and demonstrating these sorts of deceptions. [12] His book includes detailed descriptions and examples of the following types of deceptions:
| Sacm Name | Description |
|---|---|
| advanced fee scam, | You need to pay an advanced fee in order to get a prize / loan / etc. |
| advertising solicitation scheme, | You are billed for advertising that looks like something you expect, but is not real. |
| assumed identity scam, | The scammer assumes an identity and does what that identity would to to get something from you. (Like a parking lot attendant to steal cars.) |
| autograph, | Victim fooled into signing a paper later used for a forgery. |
| automated debt scam, | Unauthorized withdrawl from checking account (ATM card number make this expecially easy today) |
| bail bond con, | Midnight call posing as neighbor's friend trying to help get him bailed out of jail. Picks up money at door. |
| bait-and-switch, | Sale where items are sold out before ou get there or they try to upsell you. |
| bank examiner scheme, | Claim to be a bank examiner outside a bank trying to catch a teller who is cheating. Get the victim to take out money and give them a receipt for the cash. |
| bankruptcy fraud, | Borrow big $s and use bankruptcy to avoid debts - repeatedly - under different business names. |
| big con, | The victim is sent to retrieve funds from a bank and these funds are taken by some scam. |
| big store, | A place appears to be a buiness to bilk the victim out of money. |
| blind pool penny stock scam, | Convince the victim to invest in nearly worthless stock. The promoter keeps the price higher than the value and pockets much of the difference in a very high salary. |
| block bustle, | Selling items really inexpensively on the street (claiming they are stolen) and convince buyer not to open the box when buying (factory sealed). |
| blow off, | Get the victim to leave after they are conned by some trickery (the cops are coming - get away quickly...) |
| boiler room, | Room full of people calling on some scam or sale - the collect the money and disappear before the packages are supposed to arrive. |
| call-sell operator, | Sell long distance calls using stolen phone card numbers. |
| canister con, | Canisters collecting for a fake charity are placed in stores and picked up when full. |
| cash-back deposit con, | Use fake deposits to get cash back from a bank account. |
| cash drawer con, | You walk in with a replacement cash drawer claiming to be an auditor and get them to hand you the drawers full of cash in exchange for the nearly empty ones so you can audit them. |
| chain letter, | A letter that says send you can make money by sending them money, adding a name to the list, and sending it to 20 friends. |
| check bleaching, | Remove dollar amounts on checks and replace them with bigger figures. |
| check kiting, | Using the delay on check clearance to make it seem like you have lots of money in lots of banks. |
| circle of friends con, | Con artist takes advantage of friends and family of the victim (use victim as reference or dupe). |
| claimant fraud, | Claiming to be injured when you are not, often with the help of a doctor on the take. |
| COD scam, | COD package delivered unexpectedly - after collecting the fee, the empty package is left. |
| computer repair scheme, | Call from computer repair claiming to be there to fix something and gain entry and access to equipment. |
| counterfeit product, | Create a fake Rolex watch or some such thing and sell it for a 'great' price. |
| coupon fraud, | Fake copies of coupons are made. |
| credit repair scheme, | Promis to clean up credit ratings for a fee. |
| damage claim artist, | Pretend to be injured, threaten to sue, take a cash payoff. |
| dirt-pile scams, | Opportunity to invest in a faks gold mine (long time frames for retun on investment help get more money). |
| diverter fraud, | Healthy person buys presciption from a crooked pharmacy, sells back to the pharmacy at big discount, pharmacy collects from insurance company. |
| dummy supply company, | Create a dummy supply company and have insider send purchases through it at good prices. Build volume till you make a big buy, never fulfill, and walk with the cash. |
| file segregation, | Create new identities for people with bad credit to allow them to get more money. |
| forclosure forstallment scam, | I am being foreclosed on this huge property and all I need is $50,000 to stall it till I sell the property, which I will give you a percentage of for helping me out. You will double your money in a few weeks and save me from losing it all. |
| foreign bank investment scam, | Promise high profits for investment in foreign banks. |
| franchise fraud, | Franchiser sells franchises but never fulfills - running away with the investment monies. |
| friendship swindle, | Make friends with a relatively lonely person and start borrowing increasingly large sums of money from them over time. |
| front-end loading, | High costs for buying initial products with promise of discounts at higher volumes. |
| gold brick con, | Sell phoney gold bricks. |
| green-goods racket, | Victim pays real money for forged money. |
| home diversion game, | Two people visit (usually old) victim's house, one occupies them and the other searches for cash and jewelry. |
| hot seat, | Victim is asked to deposit a lot of cash and leaves a deposit with the con artist whoi palms the cash and provides newspaper in its place. |
| Jamaican switch, | Victim is asked top hold large sum of foreign cash for the 'foreigner' con who takes real cash as a deposit. |
| medical mills, | Medical and legal professionals work with paid patients to defraud insurance companies through false claims. |
| need-help scam, | Victim is told the person needs help and is convinced to provide money, use of car, etc. as assistance. |
| never-received issue, | Credit cards are intercepted before they get to the cardholder. |
| obituary hoax, | Visit a bereaved person and demand repayment of non-existent debt from deceased. |
| office creeper, | Break into offices at night and creep around planting Trojan horses and stealing information. |
| paper accident, | Phoney car accident submitted to car insurance company for insurance. |
| paper firm, | A fictitious company created to defraud another company. |
| phantom employee, | Create a phantom employee who gets paid but doesn;t exist. |
| pigeon drop, | Victim 'finds' cash along with two cons. One decides to ask a lawyer what to do. Phoney lawyer puts the cash in 'escrow' and holds 'ernest' money while full settlement amount is determined. |
| Ponzi scheme, | Give me $50 and I'll give you $100 in one month out of the resulting business. Do it in ever increasing volume using new income to pay off old outlays and generate lots of cash flow, then walk with the cash at some point. |
| premium diversion fraud, | Divert premium payments from real insurance comany. |
| premium fraud, | Employers steal from unemployment by lying about salaries or titles to lower premiums. |
| reinsurance scam, | Undercapitalized re-insurer lies about assets and collects big premiums which it cannot pay out on. |
| reload scam, | Victims who have fallen for phoney prize scams are called again for other scams. |
| rocks in the box, | Would you like a discount television off this truck? They show you one that's openned, then give you the factory sealed one (for cash) which contains only rocks of similar weight. |
| running the buckets, | Charge for more paint than was used by making it look like a lot more paint cans were used than really were. |
| soft tissue injury, | Act like you got hit by their car (or some such thing) and claim soft tissue injuries - use doctor on the take to support your claim. |
| staged auto accident, | Create an accident to collect on the insurance. |
| sweepstakes scam, | You have won a big prize but must pay a fee in order to collect it. |
| sweetheart scam, | Get someone with money to fall in love with you and take them for all they are worth - get married if necessary. |
| swoop and squat, | (a.k.a. bull and cow) Staged car accident to get insurance money. |
| the tat, | The victim uses regular dice while the confidence man uses loaded dice. |
| teleblackmail, | Blackmail innocent employees who have been deceived by 'toner phoners' under threat of exposing them to the boss. |
| three-card Monte, | A shill wins at the game (which uses slight of hand to palm the card you are looking for) and you lose for ever more money. |
| toner phoners, | Swindlers who sell poor quality printer toner to companies at high prices (for the quality provided). |
| trash and dash, | Dress like a maintenance person and steal information from the trash. |
| tripple-A con, | AAA person notices car problems with the victim's car (or creates them) and offers to fix them for a fee. |
| work-at-home scam, | Make money at home by stuffing envelopes, cruising the web, etc. Up front fee to learn how is stolen. |
| yank down. | Yank down items from store shelves and feint an injury as a result. |
We'll work an example to clarify. The bank examiner scheme involves someone standing outside of a bank dressed in a conservative suit with a phony identification badge and a clipboard. They get deposit slips from the bank counter. They stop customers about to enter the bank and indicate to the customers that they are bank examiners trying to catch a bank teller who is stealing by not reporting deposits correctly. To help the bank examiner, the target is asked to withdraw $100 from their account and bring it and the receipt to the 'examiner'. The 'examiner' then provides a receipt to the target and takes the money and deposit slip as evidence. The target has just handed $100 to the 'examiner' in exchange for a useless piece of paper. In a filmed demonstration, Whitlock succeeded time after time at this. Now for the analysis:
(1) The deception involves simulation by the use of a conservative suit, a phony badge, and a clipboard. This combination of items matches peoples' expectations of a bank examiner (even though most people have probably never met one). What they are asking the target to do seems in line with how one might catch a fraudulent teller and is logical in the sense that the teller might indeed create two $100 withdrawals while only handing one receipt and $100 to the customer. The deposit slip provided by the bank examiner is in line with the normal banking process of giving a receipt in exchange for cash.
(2) Except of course that in the end the person is trading $100 for a piece of paper. The problem with reasoning it out is that this is how banks always work. You give them cash, you get a piece of paper. In a large bank, the deception might even be carried out within the walls of the bank itself. The only difference is that the teller is behind the counter, and even this might be faked by having the 'examiner' stand behind one of the bank's large desks used for people to write out deposit slips.
Not surprisingly, we can create other effective schemes by following this same process. To do so, you start with a reasonable expectation - typically some behavior that people in a society carry out repeatedly without thinking too much about it every time. If the goal is to get money from them, you have to find such a behavior that involves giving someone money. If the goal is information, you need some activity used to provide information. Suppose the goal is to get a name, address, and drivers license number from someone that looks similar to you.
(1) This information is normally provided to people who get checks in exchange for good, those who are pulled over by a police official, those requesting legal forms, those involved in voter registration, etc.
(2) We pick one of these and make up a good story that could be true. Suppose we decide to go on a voter registration drive by walking through a neighborhood before an election verifying that people are registered by collecting their drivers license number (motor voter laws in many states automate registration based on drivers licenses). This is then a simulation that uses the motor voter and political situation as a form of concealment.
(3) We make sure we look the part. Go to a local election headquarters and pick up samples of brochures for your clipboard and a few campaign buttons for appearance, dress like others you see there, and hit the road - at a time when you would be home if you were working regular hours.
(4) Repeat your story, writing their information on your clipboard and asking if they want any candidate-related information. Provide any requested information. When you find someone who looks a lot like you, you have achieved your goal.
This wasn't a pre-fabricated example or one based on a real scheme in the local paper. It was made up on the spot in a minute or so and it would very likely be very successful because it follows the pattern of exploiting the normal expectation and logical reasoning process of the target. It is highly dependent on social context, and this means that in order to be effective, it must be based on reasonable intelligence estimates of the social environment and expectations.
Faron
Fay Faron points out that most such confidence efforts are carried as as specific 'plays' and details the anatomy of a 'con' [30]. There are seven ingriedients of a 'con' and anotomical components:
| Ingredient | Description | Anatomy |
|---|---|---|
| Too good to be true | Free money for doing nothing is typical | The motivation |
| Nothing to lose | Victim thinks they are holding the money | The come-on, The swap |
| Out of their element | It's in an area of expertise the victim doesn't know about | The shill |
| Limited-time offer | Some decision has to be made right away | The stress |
| References | Independent third opinion (really a shill) makes it seem legitimate | The shill |
| Pack mentality | Everyone else seems to agree on what to do | The shill |
| No consequence to actions | We will get away with it for some reason or another | The block |
| Step | Details | Example |
|---|---|---|
| 1) Find a victim (the mark) | Victims are identified by particular characteristics, such as age, condition, appearance, etc. | Old single people with little or no family are often targeted because of their high degree of susceptibility. |
| 2) Gain victim's confidence | This has to do with presentation, appeal, references, and similar things that gain confidence. | Being a 'disinterested stranger' seemingly caught up in a similar precarious situation might create mutual trust and confidence. |
| 3) Show the victim the money | Entice them with a win, or perhaps provide them a sample of affection or business success. | Maybe it's a 'golden opportunity', or perhaps just cash found on the street. |
| 4) Tell the tale | The victim is told that they can make it big, get married to their dream partner, or get whatever they desire. | Almost any story will do as long as it is credible to the victim - I am an illegal alien and I can't be seen in the bank, so if you can just do this for me... |
| 5) Deliver a sample return on investment | The victim starts to get the things they wanted. | Hey Mary, that $25 you leant me... I bet it on a sure thing and made $500. Here's 50 of it as appreciation for the loan. How would you like top be my partner in this. |
| 6) Calculate the benefits | The victim is shown how that can get so much more than they already have. | You know, if we did this again, we could make a bucket full of money. |
| 7) Send the victim for more money | They have to empty their bank account, provide everything they have, or what have you. | All I need is your cash to add to mine and we will be able to make a killing. |
| 8) Take them for all they have | You need to get away with the desired returns. | Oh no! It didn't work this time. We have both lost everything we worked so hard for. |
| 9) Kiss off the victim | Leave, perhaps in a manner so that they victim believes they got away with a good deal. | Here, you take the purse with the money, and we will meet tomorrow at the bank to finish the paperwork. |
| 10) Keep the victim quiet | Create a disincentive against reporting the incident. | Oh no! It's the cops. If they find me here with you, we will both be in a lot of trouble. You head out and I'll stall them. |
Problems tend to arise when the desired goal is far afield from the normal behavior patterns of the target(s). The reason is that this requires more simulation and concealment and more substantial changes in expectations. This in turn increases the odds of not being detected and associated with the true cause, with a resultant increased potential for failure of the deception. On the other hand, meeting or exceeding the expectations and exploiting the hopes and dreams of targets makes the deception highly likely to succeed. Ego and greed play an important role in the success of deceptions against people.
Bob Fellows
According to Bob Fellows [13] (p 14) people the following characteristics improve the changes of being fooled; (1) under stress, (2) naivety, (3) in life transitions, (4) unfulfilled desire for spiritual meaning, (5) tend toward dependency, (6) attracted to trance-like states of mind, (7) unassertive, (8) unaware of how groups can manipulate people, (9) gullible, (10) have had a recent traumatic experience, (11) want simple answers to complex questions, (12) unaware of how the mind and body effect each other, (13) idealistic, (14) lack critical thinking skills, (15) disillusioned with the world or their culture, or (16) lack knowledge of deception methods.
Fellows also identifies a set of methods used to manipulate people. The illusion of free choice is an example where the victim has choice but no matter what choice is made, as long as it fits the constraints of the person carrying out the deception, the victim will appear to have had their mind read. This is an example of posteriori proof. The deception involves a different path to the desired solution depending on the solution required by the 'free choice' of the victim. [13] p22 Mind control is exerted through social influence that restricts freedom of choice. It consists of psychological manipulation, deception, and the use of 'demand characteristics'. Demand characteristics are based on social conditioning that put pressure on the individual to act in predictable ways in properly constrained situations. For example, in a stage trick, when you ask the person to make a choice between one of two things, they are socially constrained to not choose a third option. A theater setting causes people to sit and listen while a speaker talks. Guests generally try not to complain, so by treating people as guests, you are more likely to sit and listen to my political views. Hypnosis, suggestion, absorption, fatigue, and social influence are also identified as control methods. In hypnosis, a hypnotic state is induced, while in suggestion uncritical acceptance and sometimes response to an idea is involved, while in absorption, the individual's attention is focused on an activity so that it is hard to distract them from it.
In his examination of manipulation techniques, Fellows includes; (1) Vague or tailored standard of success, (2) observation of human nature, (3) situational observation, (4) specific vs. ambiguous information, (5) information control, (6) pseudo-scientific or spiritual theories, (7) confusing normal experiences with extrasensory perception, (8) skeptical stance, (9) fishing (deception), (10) authority, charisma, and appearance, (11) misdirection, (12) humor, (13) limited paranormal claims, (14) mind body connection demonstrations, (15) selective subject responsibility, (16) probability, (17) individual tailoring, (18) dissonance reduction and self-perception, (19) compliance and suggestability, (20) shaping behavior, and (21) selective perception and recall. These are combined in a script to make a convincing case to an audience.
Thomas Gilovich
Thomas Gilovich [14] provides in-depth analysis of human reasoning fallibility by presenting evidence from psychological studies that demonstrate a number of human reasoning mechanisms resulting in erroneous conclusions. Them mechanisms identified include;
| Mechanism | Example |
|---|---|
| (0) Effects should resemble their causes, | |
| (0a) Instances should resemble their categories | Similar looking animals must be more closely related genetically than different looking ones. |
| (0b) Like resembles like | Measles come from germs with spotted coatings. |
| (0.5) Tendency toward oversimplification, | |
| (0.5a) Occum's Razor | When a simple explanation will do, choose it over the more complicated one. |
| (0.5b) Black and White | Tends to be preferred over shades of gray. |
| (0.5b) Rule of 3s | Lists of three things are better accepted in some cultures. |
| (1) the misperception of random events, | |
| (1a) the clustering illusion, | Events appear to be correlated even when they are not correlated |
| (1b) overapplication of representativeness, | The 'law of small numbers' - a few examples are taken as more signficant than they really are. |
| (1c) misperceptions of random dispersions, | Various random events are seen as 'shooting streaks' because randomness is not well understood by most observers. |
| (1d) the creation of causal theories, | People have a tendency to create thearies to explain what they see and adopt them regardless of evidence. |
| (1e) the regression fallacy, | People underestimate the effect of regresson. For example, if you usually average two sales a day and make five sales for each of three days in a row, people will think you are in a slump when you only make one or two sales a day for the next week. |
| (2) misinterpretation of incomplete or unrepresentative data, | |
| (2a) the excessive impact of confirmatory information, | A small number of confirmations are treated as proof, while an occasional refutation may be dismissed as invalid for some posteriori reason (perhaps generated 1d above). |
| (2b) the tendency to seek confirmatory data, | If you are looking for red in fires you will tend to count orange as red, and not discount the presence of blue along with red. |
| (2c) the problem of hidden or absent data, | If you justify the quality of your hiring process by tracking only the success rates of people you hire, you are ignoring the missing data on how successful the people you didn't hire might have been. |
| (2d) self-fulfilling prophecies, | If people believe the markets are crashing, they will pull their money out, and thus the markets will crash. |
| (3) the biased evaluation of ambiguous and inconsistent data, | |
| (3a) ambiguous information is interpreted in context, | We tend to interpret ambiguous data in the context of what we are looking for. |
| (3b) unambiguous data is shaded, | An explanation for the invalidity of data that is inconsistent with theories is often found. |
| (3c) multiple endpoints, | If the data is ambiguous we will tend to associate it with our expectations for outcomes, thus biasing the result. For example, some element of a baby's face looks like anyone and will be associated with the parents face even if the child is adopted. |
| (3d) confirmations and non-confirmations, | Non confirmations are often ignored rather than treated as refutations. Selective memory is an example where people will tend to remember predictions that come true over time and forget those that do not come true. |
| (3e) focused and unfocused expectations, | If we believe that bad things come together in threes but don't set a time limit on what it is to come together, we will wait till the count hits three and declare that we were right. If we are trying to associate a dream of a sunny day with events of the day, we will find the moment that the sun broke through the clouds as a confirmation. |
| (3f) outcome asymmetries and one-sided events, | |
| (3f-i) hedonic asymmetries, | There is a tendency to overemphasize things that are more striking to us. For example, it may seem like you almost always get splashed by a passing car on wet days, when in fact you just remember being splashed more than not being splashed. |
| (3f-ii) pattern asymmetries, | You remember when you wake up and see 1:11 or 2:22 on the clock better than when you see 1:52 or 2:17 |
| (3f-iii) definitional asymmetries, | Things won't get better till you have hit rock bottom - but since 'rock bottom' is not pre-defined, it is always able to be true since we can call wherever you turned around, 'rock bootom'. |
| (3f-iv) base rate departures, | "Thinking about being healthy will help you cure cancer" is supported by people who have thought about being healthy and survived, but it ignores the people who thought about being healthy and died, because they are not available as data points. |
| (4) motivational determinants of belief, | |
| (4a) empirical support for the wish to believe, | After the Nixon / Kennedy debates, supporters for each side thought their side had one. They interpreted the same thing in different ways. |
| (4b) mechanisms of self-serving beliefs, | If you want to believe it you ask "Can I believe it" while if you don't want to believe it you ask "Must I bnelieve it". |
| (4c) optimistic self-assessment | The vast majority of people believe they are above average in intelligence and beauty. |
| (5) the biasing effect of second hand information | |
| (5a) sharpening and leveling, | In relaying situational information, descriptions of peoples' behavior tends to be 'sharpenned' or emphasized, while descriptions of their surroundings tend to be 'leveled' or de-emphasized. |
| (5b) the corrupting effect of increasingly indirect evidence, | The game of 'telephone' is a great example. |
| (5c) telling a good story, | In order to make the story interesting to the audience, distortions are often introduced. The 'historical movies' that come out of hollywood are examples of how telling a good story often distorts facts in favor of 'flavor'. |
| (5d) distortions in the name of informativeness, | Stories are often told with exagurations of the fact to make a point. A little girl down the block did than and she was never seen again... |
| (5e) distortions in the name of entertainment, | 'There is one example of...' becomes 'I had a friend who...' and the audience misinterprets it as if their own friends probably... Inquiring minds want to know... The media is notorious for this. |
| (5f) distortions in the name of self interest, | Look at the statements of political parties. |
| (5g) distortions due to plausibility, | So-called urban legends are good examples of this - for example the non-existent US patent agent who supposedly resigned because he thought that nothing else could be invented. |
| (6) exaggurated impressions of social support, | |
| (6a) social projection and the false consensus effect, | Most people think that most other people agree with them about their views on things. |
| (6b) inadequate feedback from others. | People may agree out of politeness or not indicate that they disagree because of a desire not to offend. Children show less of this than adults. |
These mechanisms are detailed and supported by substantial evidence and most of them are believed to be common to most individuals in all human societies.
Charles West
Charles K. West [32] describes the steps in psychological and social distortion of information as consisting of:
| Step | Details | Subtypes |
|---|---|---|
| A | An unlimited number of problems and events in reality. | The whole universe and all of the varuous effects of the wave equations at every scale. All of physics effects us. |
| B | Human sensation can only sense certain types of events in limited ways. | This includes Hearing, Sight, Smell, Touch, and Taste - the so-called five senses. |
| B.1 | Hearing | Hearing is limited in frequency range, resolution, and discrimination. |
| B.2 | Sight | Sight is limited in frequency range, resolution, and discrimination. |
| B.3 | Smell | Smell is limited in chemical combinations and discrimination. |
| B.4 | Touch | Touch is limited in sensitivity, sensor d\istribution, and pressure differentiation. |
| B.5 | Taste | Taste is limited in chemical combinations and discrimination. |
| C | A person can only preceive a limited number of events from B at any moment. | There are three ways in which the nerve system limits the transmission of sensory impulses to the brain; habituation, inhibition, and Hernandez Peon effects. |
| C.1 | Habituation | Habituation tends toward ignoring repeated senses. |
| C.2 | Inhibition | Inhibition limits the effect of other sensors proximate to a high firing rate sensor. |
| C.3 | Hernandez Peon effects | Hernandez Peon effects limit the ability to use one sense when focussing on another sense. |
| D1 | A person's knowledge and emotions partially determine which of the events in C are noted. Interpretations of C are made in terms of knowledge and emotion. | Frame of reference and experience drives the sequence of focus. This includes concepts, structures, affects, needs, values, and interests. |
| D1.1 | Thought: Concepts | Awareness combined with meaning or significance. For example, when a set of words are presented to test subjects before performing a complex task, if some of the words presented in order might help solve the task, the subjects are more likely to do a better job of solving the task sooner. They have somehow mapped the words into a concept allowing a more rapid and more effective solution. |
| D1.2 | Thought: Structures | Conventions and standard ways of going about things. A very good example is that when shown the same ambiguous stimulus, people from different cultures will see different objects. Similarly, when presented with audio giberish in repeated patterns, people will hear different word sequences and those sequences will change with time. Similarly, when structures exceed memory capacity, people create organization schemes to allow them to be remembered (7+/-2). |
| D1.3 | Feeling: Affects | Likes, dislikes, happiness, sadness, afraid, etc. states of mind effect ability to recognize words, etc. |
| D1.4 | Feeling: Values | Fairness, right and wrong lead to changes in attitude and acceptance of new information. |
| D1.5 | Feeling: Needs | Lack of food, water, sugars, air, etc. lead to reduced learning capacity, increased association of sensory data to need-related information. |
| D1.6 | Feeling: Interests | More interest leads to better learning. |
| D2 | A person's perceptions of C may also be influenced by group norms and social pressure. | Frame of reference and experience drives the sequence of focus. This includes |
| D2.1 | Reinforcement | The group sets punishments and rewards. Authority and percentage and size of group agreeing, while education and high ethics reduces conformance. |
| D2.2 | Imitation | There are rewards for perceiving and acting like the group and punishment for not seeing and acting like the group. You might learn what to do (initiating) or learn what not to do (inhibiting). |
| E | Intentional bias as a person consciously selects from D1 and D2 that which will be communicated to others. | This is also known as lying. |
| F | The receiver of information provided by others will return to step C and all other steps may be repeated. |
Thus more distortion results from the inadequacy of language to describe reality, the incommersurability of experience between people, and the distortions of language bias. |
Al Seckel
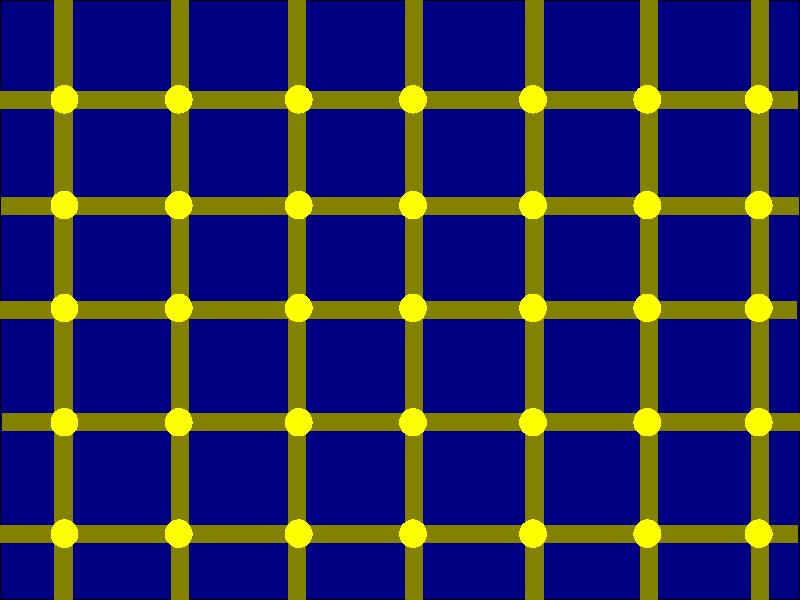
Al Seckel [15] provides excellent examples of various optical illusions, many of which work regardless of the knowledge of the observer, and some of which are defeated once the observer sees them once. While some of these illusions have unknown mechanisms, many of them are based on physiological aspects of human optical sensory and interpretation mechanisms. These include receptor fatigue, contextual clues, perspective, scintilation, color averaging, shade averaging, false triggering of horizontal or vertical motion detectors, priming illusions, context size illusions, shaddow illusions, upside-down vs. right side up facial recognition mechanisms, afterimages of various sorts, twisted cord illusions, and the plank illusion. An example illusion called the scintillating grid is provided here as an example.
Chester Karrass
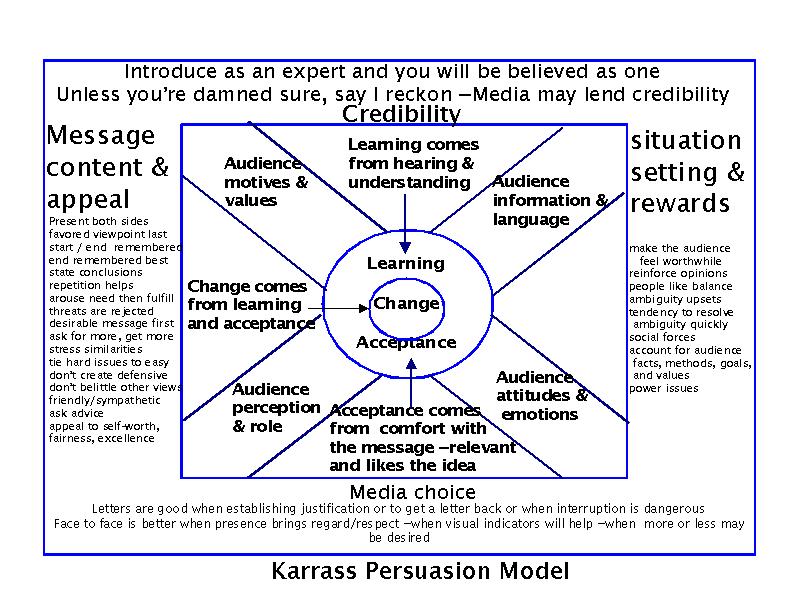
First Karrass [33] then Cialdini [34] have provided excellent summaries of negotiation strategies and the use of influence to gain advantage. Both also explain how to defend against influence tactics.
Karrass [33] explains that change comes from learning and acceptance. Learning comes from hearing and understanding, while acceptance comes from comfort with the message, relevence, and good feelings toward the underlying idea. These are both affected by audience motives and values, the information and language used for presentation, audience attitudes and emotions, and the audience's perception and role in the negotiation. By controlling these factors, advantages can be gained in negotiations. Additional factors include:
-
(1) Credibility of the presenter helps gain advantage and it attained by suitable introduction and historical behavior;
-
(2) Message content and appeal are gained by (a) presenting both sides with the favored viewpoint at the start ane end, (b) repetition of the points to be made, (c) stating conclusions, (d) arousing a need and then fulfilling it, (e) avoiding threats, which tend to be rejected (f) asking for more, which tends to get you more, (g) stressing similarities, (h) tying hard issues to easier ones, (i) not creating defensive situations, (j) not belittling other views, (k) being friendly and sympathetic, (l) asking for advice, and (m) appealing to self worth, fairness, and excellence;
-
(3) Situation setting and rewards also play important factors and can be enhanced by (a) making the audience feel worthwhile, (b) reinforcing pre-existing opinions, (c) presenting a balance of ideas, (d) avoiding or offering to remove ambiguity, (e) using social pressures to your advantage, (f) accounting for audience facts, methods, goals, and values, and (g) understanding and dealing with issues of power and influence.
-
(4) Media choice for messages can also be important. (a) Letters are good when establishing justification, for getting letters back, for establishing justification, and when interruption is dangerous, (b) face to face is better when personal presence brings regard or respect, when visual indicators will help, or when more or less information may be desirable. (Karrass was writing before FAXes and Email were widely available).
Karrass [33] provides a three dimensional depiction of goals, needs, and perceptions and asserts that people are predictable. The three dimensions he identified are:
-
Goals: (1) Money, (2) power and competence, (3) Knowledge, (4) achievement, (5) excitement and curiosity, (6) social, (7) recognition and status, (8) security and risk avoidance, and (9) congruence.
-
Needs: Maslow's Needs Hierarchy includes (1) basic survival, (2) safety, (3) love, (4) self worth, and (5) self-actualization.
-
Perception: Perception of goals include: (1) How do you want opponents to see you, (2) how do opponents see their goals, (3) how do you see opponent goals, (4) how do you want opponents to see your goals, (5) how do you think opponents see your goals, and (6) how do you see your goals.
The object of a successful negotiation is to optimize how everyone sees their goals.
Karrass [33] also lists a series of specific negotiation techniques and countermeasures, and his work has been widely hailed as seminal in the field. Millions of people have now been exposed to his work. Some of the specific tactics he describes include:
| Type | Tactic | Description | Effect | Countermeasure |
|---|---|---|---|---|
| Timing | Patience | Willing to bear with the situation for as long as it takes. | Lowers expectations of rapid progress, may cause a desire to yield more rapidly to make progress. | More patience, loss of value with time, increased social pressures. |
| Timing | Deadline | Time limits on completion of the negotiation may drive to concessions. Many times the one with more time goes by the other parties' deadline, thus making it harder to 'win'. | Whoever has longest can take advantage. | Don't reveal deadlines, or set other parameters to limit negotiation points. |
| Timing | Speed | Quick agreements can be made on small points, one after another, until there are no points left to be agreed upon. | Causes a pattern of saying yes which carries through to future issues that may not have yielded a yes and creates an expectation of rate of progress. | Quick counteroffers, refusal to make partial agreements, or a slowing of the process. |
| Timing | Fait accompli | Actions that alter the balance of bargaining power by virtue of already being in place, thus making them far harder to undo. | Reduces expectations, increases work to change things. | Tit-for-tat reprisals, demonstration of willingness to undo what seems nearly impossible to undo. |
| Timing | Surprise | New conditions or requireements are added after part of the negotiation is completed. | Lowers expectations and changes the value of previous sub-agreements. | Changes require restart of the whole negotiation process, make similar changes to previous positions, make unrelated changes that gain back whatever is lost. |
| Timing | Status quo | Go with the same agreement we had before unless and until the new agreement is completed. | Lower expectations for new agreement, bypass deadlines. | Go on strike, indicate that the deadline ends the old agreement, go with the old agreement with an 'adjustment' for changes in condition (cost of living increase is an example). |
| Timing | Stretchout | Deliberate extension of negotiation over a long time. | Force the opponent to expend resources, create internal friction, increase pressure for agreement. | Walk away, start taking desirable issues off the bargaining table, start increasing the price, other time dependent reduction in opponent expectations. |
| Inspection | Open inspection | Unlimited inspection is permitted. | Openness, honesty, nothing to hide. | Do inspections and verify it. |
| Inspection | Limited inspection | Access for inspection is limited at the control of the party being inspected. | We are open, but we won't let you look around forver before making progress. | If limited inspetions are inadequate, so indicate. |
| Inspection | Confession | Full disclosure of all known items of interest are made. | Openness and honesty is laudible. | None needed except verification. |
| Inspection | Qualified confession | Questions are answered but faults are not offered. | Appearance of openness but information is only selectively revealed as needed. | Ask a lot of quesitons, including general ones like 'Are there any other things that might be relevant..." |
| Inspection | Third party | Access by agreed upon neutral third parties. | We are open and honest, but we have legitimate reasons for limiting your access. | Question sincerity, find a good inspector. |
| Inspection | No admitance | No inspection os permitted. | Reduction of expectations / can be used to cause mystique. | Go elsewhere, require alternatives to inspections. |
| Authority | Limited authority | The person at the table is not authorized to make the final deal. | It allows negotiation toward the best we can get from you, followed by having to get more from you. | If authority is know ahead of time, provide a non-authoritative negotiator on your side. If this is revealed after negotiations are underway, treat as a possible deception. |
| Authority | Approval | The person at the table can negotiate, but the deal requires approval. | Lowers expectations of finality, creates potential for refusal to approve, allows negotiator to 'blame' on someone else, allows negotiator to act like they are on your side. | Seek approval at every step, negotiate in good faith to a final agreement and refuse to take less, indicate that you too need approval and get their approval first. |
| Authority | Escalation approval | Deliberate creation of additional approvals. | Lowers expectations, an escalation of the items in "Approval". | As in "Approval". |
| Authority | Missing man | Deliberate absence of person with final authority. | As in "Approval" | As in "Approval" or indicate that you will be willing to reschedule for when the final authority is available. |
| Authority | Arbitration | Third party decision - neutral or biased. | Create at least the illusion of impartiality and fairness, lays blame on others. | Refuse to permit it, accept a well known mechanism, accept only really trusted third parties, back out. |
| Association | Alliances | Strong partners | Strengthen bargaining power, strong desire for mutual benevolence. | Foster this. |
| Association | Associates | Friends | Slight strengthening of bargaining power. desire for mutual benevolence. | Foster and improve this, ask for references. |
| Association | Disassociates | Mutual non-friends | The enemy of my enemy is my friend. | Use caution - it is not always true. |
| Association | United Nations | Broad-based alliance of industry members. | Strength in numbers. | Try to use it to improve ties, gain reference information. |
| Association | Bribery | Payoff and collusion | Someone pays someone for an advantage. | Report to law enforcement, report to management, refuse to deal with them, take their money (legally only - give them a receipt and fair market value) and don't weaken your position. |
| Amount | Fair and reasonable | Everyone wants to believe they are fair and reasonable. | Appeal to morality and sense of fairness. | Get select examples of competitors and raise price to meet theirs, provide explanations for why yours is fair and reasonable at a higher price. |
| Amount | Bulwarism | Take it or leave it. | Expectations are forced toward win or lose - no shades of gray. | Leave it. |
| Amount | Nibbling | Take small concessions one after another - after other issues are settled. | Many seemingly small items come out to a large difference. | Nibble back. For every nibble, extract a price. |
| Amount | Budget bogey | My budget is only so much. | Puts artificial limits on price. | Offer lower-quality alternatives that meet the budget, help them increase the budget, spread over multiple budget items or cycles. |
| Amount | Blackmail | Since you have no choice, they can ask whatever they want - up to a limit. | Investment in this line leaves you with little choice. | Change directions, nibble for other concessions, change other terms, walk away. |
| Amount | Escalation | After agreement, take your part and raise demands. | Lowers expectations and feelings of self-worth | Return fire - don't let them get away with it - Offer accepted is a legal contract - etc. |
| Amount | Intersection | Tie together otherwise seperate negotiations. | Creates complexity and opportunity for tying easy things to hard ones. | Refuse to tie, tie still other items, deal with the increased complexity, etc. |
| Amount | Non-negotiable | Select items can not be altered. | Lowers expectations with respect to those items and creates automatic wins for one side. | Don't buy into it, create your own non-negotiables, negotiate harder for other items, walk away. |
| Amount | Chinese auction | Multiple opponents are played off against each other. | Creates competition between competitors. | Ignore the others and negotiate for yourself, walk away, explain that after they have their best offer elsewhere, if they want to deal with you, you will be available to discuss it, trade price for other terms. |
| Brotherhood | Equal brothers | Based on equal status. | Expectation of tit for tat. | Fulfill expectation with appropriate caution. |
| Brotherhood | Big Brother | Benevolence based on higher status. | Since I am so much bigger I will help you. | Thanks, I could use the help. |
| Brotherhood | Little brother | Charity desired based on lower status. | I am small and you are big, please be nice. | Recognize that they are potentially exploiting your desire to be good. |
| Brotherhood | Long-lost brothers | Search for relationship and status. | Trying to find common ground. | Provide it. |
| Brotherhood | Brinkmanship | Intersecting destiny based on high joint risk. | Threat-based and potentially very dangerous. | Decide oif it is worth it and if so expect serious consequences and prepare for them. |
| Detour | Decoy | Attract or snare | Seemingly excellent offer is used to get you to invest time and effort which you are then motivated to get value for. | Recognize and walk away, negotiate harder to get back full value, set parameters and expectations appropriately so that you are not snared. |
| Detour | Denial | Negation or retraction of statement. | Create false impressions, generate concessions to indicate real parameters, lower expectations, increase anger and frustration, create delays. | On the first time, indicate displeasure, and take back all of the previous discussions, create pressure on their side to stop it. |
| Detour | Withdrawl | Walk away from negotiations. | Lowers expectations, may generate wild concessions just to get you back to the table. | Don't give in, create social pressures to bring them back, seek out alternative deals. |
| Detour | Good and bad guys | Good cop bad cop. | You confide in the friendly one, who looks good in comparrison to the unfriendly one. | Recognize the tactic and don't be offended or fooled by it. |
| Detour | False statistics an errors | Creating deceptive statistics | The statistics have the appearance of authority. | Question, understand, and verify this sort of information. |
| Detour | Scambled eggs | Creating dilliberate confusion on issues or figures | Confusion is used to cause the negotiator to make mistakes and get in over their head. | Know when you don't know enough and ask for help, bring in experts, explain that it is getting too complex and that if it isn't simplified, you will have to seek alternatives. |
| Detour | Low balling | Initial low price with high add-ons (close to bait and switch) | Create expectation of low price and momentum to buy, followed by seemingly small adjustments that add up. | Try to get the add-ons for free, nibble at the add-ons, get the 'whole' price and then compare it to alternatives. |
| Detour | Scoundrel | Larceny by never-ending negotiations | Wastes time and effort while consuming your resources. | Detect and walk away. |
Karrass also provides a list of negotiating techniques including: (1) agendas, (2) questions, (3) statements, (4) concessions, (5) commitments, (6) moves, (7) threats, (8) promises, (9) recess, (10) delays, (11) deadlock, (12) focal points, (13) standards, (14) secrecy measures, (15) nonverbal communicaitons, (16) media choices, (17) listening, (18) caucus, (19) formal and informal memorandum, (20) informal discussions, (21) trial ballons and leaks, (22) hostility releivers, (23) temporary intermediaries, (24) location of negotiation, and (25) technique of time. [33]
Cialdini
Cialdini [34] provides a simple structure for influence and asserts that much of the effect of influence techniques is built-in below the concious level of most people. Some factors cross all human societies, while others may be more affected by social norms and culture. Cialdini discusses both the benefits of these natural tendencies and their exploitaiton by professionals for gaining compliance to desired behaviors. Regardless of how they are created, these techniques are apparently pattern matching phenomena that operate without regard to deep logical thought processes:
| Area | Technique | Explanation |
|---|---|---|
| Recirprocation | If it costs more it is worth more | Raising the price on many items increases their sales because the buyers are looking for high quality and associate it with price. |
| Authority | Experts know more than others | When someone believes you are an expert, they will tend to defer to your opinions regardless of the sensibility of those opinions. |
| Contrast | Contrast principle | Substantial differences tend to be exagurated. Things are taken relative to context. After having your hand in hot water, luke-warm water seems cool. To sell something expensive, start by offering something more expensive and work your way down. |
| Automaticity | Because | When you add a 'because' followed by no new information, the chances of compliance increase substantially. |
| Recirprocation | Reciprocation | People tend to reciprocate any gifts. For example, even a meaningless gift will create an obligation. Refusal to accept a return gift makes you less likable because of the lack of opportunity to reciprocate. |
| Reciprocation and Contrast | Reject and retreat | This invokes both reciprocation and contrast. You start by asking for something big, then lower the request to something smaller. By reducing your request, you are both giving a concession (reciprication leading them to offer you something) and by lowering from a higher value you are invoking contrast (the second request doesn't look as high next to the first one). |
| Commitment and Consistency | Commitments are honored | If you can generate a promise of some sort, there will be a strong desire to fulfil it - no matter how much effort it takes or under what circumstances the promise was given. |
| Commitment and Consistency | Consistency is highly valued | Once you commit, your interpretation of inputs tend to support that committed view. |
| Automaticity | Desire not to think | If it requires thinking and they can back down to a simple rule of behavior, they will try to do so. |
| Automaticity | Strong desire not to rethink | If it requires rethinking, it introduces self-doubt and will be avoided unless absolutely necessary. |
| Automaticity | Default decision process | Logic is only used if there is a desire and ability to analyze the situation, otherwise, pattern matching to known social behavioral patterns is used. |
| Commitment and Consistency | Small commitments lead to big ones | Self-image is raised through making and keeping to commitments and as a result, larger and larger commitments are made over time. |
| Commitment and Consistency | Active commitments are better than passive ones | Commitments where you do something are far more effective at gaining subbsequent compliance than those which are passive promises. |
| Commitment and Consistency | Public image leads to self image | Written statements are given more credence than oral ones - both by author and reader, there is a higher tendency to do something if you write it down, public commitments are more often kept than private ones. |
| Commitment and Consistency | Increased complicance with investment | Invested time and effort (sunk costs) forms increased commitment; more pain involved increases commitment level (loyalty from hazing, more pain more gain), less external return forces more internalization of value (ownership and commitment follow), low-balling works (get a commitment, create other supports for the decision, then remove the original motivation and the commitment remains). |
| Commitment and Consistency | Consistency causes decisions | Even when remaining consistent seems foolish, people will choose new reasons to stay with a decision because to do otherwise would cause you to have to admit you were wrong and rethink your previous commitments. |
| Social Proof | We interpret based on how others interpret | Laugh tracks work even if we know they are in use. Seeded collection boxes cause increased donations. Popularity is taken as goodness, even if known to be wrong. |
| Social Proof | Social proof replaces hard proof in uncertainty | Fear is reduced by watching others like you not fear it. Create uncertainty and generate social proof. Social proof works better when they are like you. |
| Liking | We like saying 'yes' to people we like | Twice as likely to say yet to people we like, referals from friends increase likelihood of succes in sales, MCI 'friends and family' is 90% effective because it 'does a friend a favor' to switch. |
| Liking | Physical attraction increases liking | We are more likely to like someone we are physically attracted to and likely to dislike someone we are not physically attracted to. |
| Liking | Similarity breeds liking | Similar dress, color, background, behaviors, accents, lifestyle, interest, age, religion, pllitics, and names are all examples of how similarities increase liking and differences decrease liking, even when known to be falsehoods. |
| Liking | Compliments increase liking | Even when compliments are known to be deceptions, people still like those who give them - unless they go 'too far'. |
| Liking | More contact increases liking | Familiarity improves likeing unless the experience is unpleasant. |
| Liking | Groups working together bond | Common cause increases liking and friendship between group members and groups. |
| Liking | Groups in competition breeds enemies | Competition creates hostility and personal dislike. |
| Liking | Messages are attributed to messengers | When a message is unpleasant, the messenger is disliked, while good messages cause mesengers to be liked. The attributes of the message are attributed to the mesenger by association. |
| Liking | Association enhances liking or disliking | People are more receptive to compliance after a good meal. People associate to their nation, city, race, etc. and like it when the things they associate with succeed. |
| Liking | People tend to associate with things that enhance their self-image | If they like themselves, they choose to associate to things that are successful through the similarities to themselves. If they have a negative self-image they tend to associate with things that fail by seeking similarities with themselves. |
| Authority | Duty to authority is deeply embedded in culture | Higher authority overrides lower ones, appearance of authority replaced real authority, titles lead to the appearance of authority, higher deference to known authorities. |
| Authority | Appearances imply authority | Higher position appears to be taller, taller as more important, importance seen as larger, larger size implies more strength. clotinh and accoutraments imply authority (as a function of situation), other trappings imply authority. |
| Scarcity | Perceived scarcity increases perceived value | Similar to Shannon's information theory in which less frequently used syntax elements have higher informaiton content. Scarce quantity, time, availability all make things more attractive. |
| Scarcity | Loss is higher value than gain | In trading a loss against an identical valued gain, the loss is more highly valued. |
| Scarcity | Desire to have what is restricted | Especially effective against teenagers and young children, but also quite effective against people of all ages. More effective if more restrictive. Exclusivity yield desire to have. |
| Scarcity | Desire to have it "our way" | Even if 'our way' is actually not 'our way', the fact of choice increases desirability. |
| Scarcity | Exclusive information is more valued | Secrets, information that others do not have, restricted information, all seem to make the information more valuable. Exclusive information about a shortage has more effect on driving up perceived value that the shortage itself. |
| Scarcity | Drops from abundance to scarcity increase value | More value is attributed to something if it is first possessed then lost. For example, revolutions are far more likely after some political gains followed by retrenchment. |
| Automaticity | automaticity can be enhanced | Incresed rush, stress, uncertainty, indifference, distraction, and fatigue all lead to less thoughtful and more automatic responses. Thus by adding to these elements, we increase the effectiveness of all of these techniques. |
While Cialdini backs up this information with numerous studies, his work is largely done and largely cites western culture. Some of these elements are apparently culturally driven and care must be taken to assure that they are used in context. Similar studies for people interacting with and through computers have not been completed at this time as far as we can tell but they would clearly be helpful in understanding how people interact through and with computers.
Lambert
By returning to Lambert's model of cognition, we can fit specific elements of the behavioral characteristics and methods of deception described above into the model of cognition. Specifically, we can find instances where sensory information is either (1) concealed in which case further consideration or response is supressed, (2) simulated in which case further consideration or action are induced, and (3) a given level is not affected and thus cognition continues as it would have without the deception.
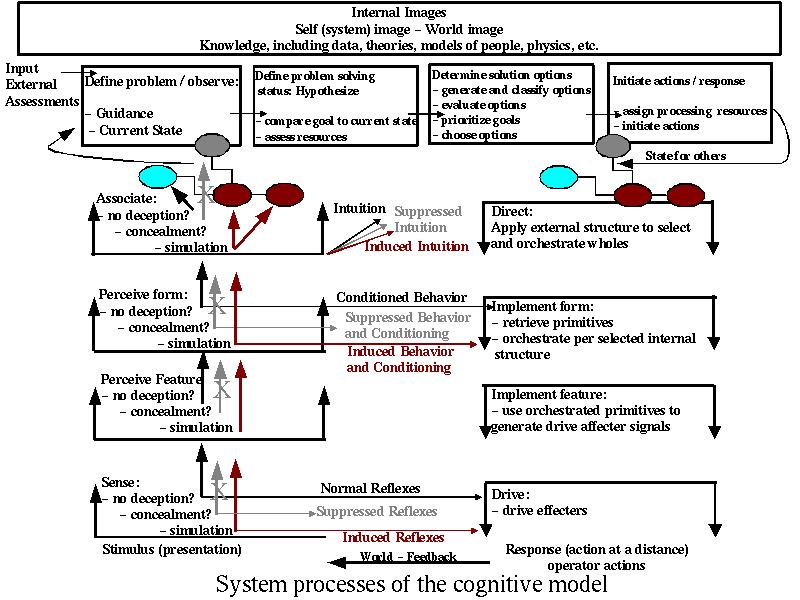
Lambert's Cognitive Model with Deception Options
The net effect of such a modeling effort provides the means to specifically associate cognitive functions with deceptions. This will potentially allow us to analyze deceptions in detail, create counter-deception methods, create numerous deception scenarions, and describe deceptions in cognitive terms.
Robertson and Powers
Robertson and Powers [31] have worked out a more detailed description of cognition based on "Perceptual Control Theory" (PCT). In this theory, perception and behavior in humans are described as a control system with multiple levels of hierarchy. Based on experimental demonstrations that indicate that at least 10 orders of control exist (and are developed as part of development) in humans, they provide a speculative description of PCT which we summarize in the following chart:
| Order | Name | Description |
|---|---|---|
| 1 | Intensity | This is a single value associated with magnitude of any signal in the overall control system. In the brain, it corresponds roughly to the chemical concentrations of neurotransmitters, temperature, and signal train emitted from neurons. In PCT, it is roughly in correspondence to the frequency of firing of neurons due to stimulus and environment. |
| 2 | Sensation | This roughly corresponds to level 1 in Lambert's model - the sensor and affector level. At this level, according to PCT, you perceive features such as color, brightness, loudness, and so forth, but it is not related to other things. For example, at this level, shapes are not formed and sensed items are not related to each other. PCT does unfortunately little description of the control mechanisms or what sorts of motor actions they imply at this level, however, we speculate that there is a sort of reflexive response at this level, such as the closing of eye lids in response to high intensity light levels. There are many stimuli in the physical world, and systems have sets of sensors. We often talk as though one type of stimulus (Intensity) affects each kind of sensor (Sensation #1) in a particular way (Sensation #2), but, in general, it's not clear that there is necessarily a correct order for Intensity and Sensation. Each stimulus may affect multiple sensors (e.g., a loud noise may be heard, felt, and perhaps even seen (e.g., if it puts pressure on the eye.) From the system's perspective, in general, a given deployed sensor (sensation is the first order) may sense multiple kinds of stimuli (e.g., a strain gauge may be sensitive to position, temperature, sound waves may cause it to move, etc. and a sonar array may be sensitive to sounds and other vibrations and pressure gradients). The eye is sensitive to red light and green light (sensitivity first, intensity second). In any given system, we may think of each sensor picking up a weighted sum of the stimuli. Each affector may drive a weighted sum of multiple kinds of real world changes and each qualitative kind of real world change may be influenced by a weighted sum of a variety of kinds of affectors. |
| 3 | Configuration | This seems to be somewhat arbitrary and poorly defined in PCT. It is beyond the authors' physical knowledge of how the brain functions and is associated only with grouping of some ill defined sort. The feedback mechanisms at this level are also undefined by the authors, but they do notion about feedback being the cause of the ability or inability to distinguish shapes based on relative brightness and other similar factors. Roughly speaking, this corresponds to the Feature and Form levels in Lambert's model. |
| 4 | Transition / Motion | This notion introduces change into the model, in that it assumes static notions of things like color and shape from 'lower' levels and asserts that some sort of difference signals are provided to indicate motion. Physiology tells us that there are physiological signals generated by things like movements of lines, but no specifics are provided in the PCT model. Again, no notions are expressed about how the feedback mechanisms at this order of perception work. |
| 5 | Events | PCT defines an event as a unitary package of elements from lower levels of the hierarchy having a familiar pattern in time. This is where stimulus-response pairings often occur. This appears to correspond to the 'Association' level in Lambert's model. The only feedback mechanism provided here is a generic 'response', without any details of how this might happen or how the response is a natural side effect of a fifth order control system but not of a fourth order control system. |
| 6 | Relationships | This PCT order seems to have to do with ordering, as opposed to the 'lower' order which corresponds to proximity in time. It is unclear why these two orders are differentiated, but it seems to be related to the tendency of the authors to use introspection as their evidential basis. This order is also used to explain relationships like 'on', 'under', 'near', and so forth. Somehow this notion is related to linguistic semantics, but the authors do not so indicate. |
| 7 | Categories | This is described as the general grouping of things together into sets of things with similar characteristics. These are what we generally associate with the linguistic notion of a noun. This seems to be similar to Lambert's Association level. |
| 8 | Sequence / Routines | This level is used to describe patterns with beginnings, middles, and ends. It roughly corresponds to Lambert's Association level. |
| 9 | Program / Branching Pathways; Logic | This level assumes an 'if then else' type of structure, or at least a set of branches with different triggering mechanisms. This is similar to the 'production system' of computer science. This is viewed as a purely logical mechanism, which seems to ignore half of the brain. |
| 10 | Principle | This is the correlation of decisions from the lower leves into 'rules of thumb', like "don't spit into the wind". |
| 11 | System Concept | This is described as reasoning about programs, something the authors assert computers haven't been programmed to do yet, but of course they have since the 1950s. |
One determines whether/what type of perception is under control by (1) disturbing it and seeing whether the organism tries to bring it back to its original value; (2) notice the speed of control (first order control systems are very fast (10 Hz); second order at 3 Hz, Third order = overshooting when reaching for something; (3) notice whether there is variability that is an indicator of corrections being applied. (p. 126)
Summary
To briefly summarize, there is a lot of evidence supporting the nature of the perception process as involving limitations in a variety of perception areas and a set of feedback mechanisms with characteristics that are only partially understood today. While we will continue to learn more as we understand more about the functioining of the brain, there is already a rich set of characteristics which we can work with in evaluating and understanding the issues behind deception in humans. For the time being, we will be continuing to use variations on Lambert's oritinal model because it is the one that has been most richly explored in terms of deception. We anticipate that this model will continue to be adapted over time to meet new information as it comes to light.
The one vital adaption that is required for Lambert's model to be suitable for our use is the inclusion of control signals of some sort affecting all of the perceptions levels. It would appear that affectors must alter the behavior of perceptors for this model to be accurate to the needs of deception.
ORG
***** WE NEED TO ADD THE ORGANIZATIONAL MODELS HERE IN DETAIL
Greene
Greene [46] describes the 48 laws of power and, along the way, demonstrates 48 methods that exert compliance forces in an organization. These can be traced to cognitive influences and mapped out using models like Lambert's, Caldini's, and the model created for this effort.
| Number | Saying | Content |
|---|---|---|
| Law 1 | Never outshine the master. | Always make those above you feel comfortable in their sense of superiority. In your desire to please or impress them do not go too far in displaying your talents or you might accomplish the opposite - inspire fear and insecurity. Make them appear more brilliant than they are - and you will attain the heights of power. |
| Law 2 | Never put too much trust in friends, learn how to use enemies. | Be wary of friends - they will betray you more quickly, for they are easily aroused to envy. They also become spoiled and tyrannical. But hire a former enemy and he will be more loyal than a friend, because he has more to prove. In fact you have more to fear from friends than from enemies. If you have no enemies, find a way to make them. |
| Law 3 | Conceal your intentions. | Keep people off balance and in the dark by never revealing the purpose behind your actions. Without a clue as to what you are up to, they cannot prepare a defense. Guide them far enough down the wrong path, envelop them in enough smoke, and by the time they realize your intentions, it will be too late. |
| Law 4 | Always say less than necessary. | When you are trying to impress people with words, the more you say, the more common you appear, and the less in control. Even if you're saying something banal, it will seem original if you make it vague, open-ended, and sphinxlike. Powerful people impress and intimidate by saying less. The more you say, the more likely you are to say something foolish. |
| Law 5 | So much depends on reputation - guard it with your life. | Reputation is the cornerstone of power. Through reputation alone you can intimidate and win; once it slips, however, you are vulnerable, and will be attacked on all sides. Make your reputation unassailable. Always be alert to potential attacks and thwart them before they happen. Meanwhile, learn to destroy your enemies by opening holes in their own reputations. Then stand aside and let public opinion hang them. |
| Law 6 | Create an air of mystery. | Never make it too clear what you are doing or about to do. Do not show all your cards. Mystery and uncertainty create anticipation - everyone will want to know what comes next. Use mystery to beguile, seduce, even frighten. |
| Law 7 | Get others to do the work for you, but always take the credit. | Use the wisdom, knowledge, and legwork of other people to further your own cause. Not only will such assistance save you valuable time and energy, it will give you a godlike aura of efficiency and speed. In the end your helpers will be forgotten and you will be remembered. Never do yourself what others can do for you. |
| Law 8 | Make other people come to you - use bait if necessary. | When you force the other person to act, you are the one in control. It is always better to make your opponent come to you, abandoning his own plans in the process. Lure him with fabulous gains - then attack. You hold the cards |
| Law 9 | Win through your actions, never through argument. | Any momentary triumph you think you have gained through argument is really a Pyrrhic victory: the resentment and ill will you stir up is stronger and lasts longer than any momentary change of opinion. It is much more powerful to get others to agree with you through your actions, without saying a word. Demonstrate, do not explicate. |
| Law 10 | Infection: avoid the unhappy and unlucky. | You can die from someone else's misery - emotional states are as infectious as diseases. You may feel you are helping the drowning man but you are only precipitating your own disaster. The unfortunate sometimes draw misfortune on themselves; they will also draw it on you. Associate with the happy and fortunate instead. |
| Law 11 | Learn to keep people dependent on you. | To maintain your independence you must always be needed and wanted. The more you are relied on, the more freedom you have. Make people depend on you for their happiness and prosperity and you have nothing to fear. Never teach them enough so that they can do without you. |
| Law 12 | Use selective honesty and generosity to disarm your victim. | One sincere and honest move will cover over dozens of dishonest ones. Open-hearted gestures of honesty and generosity bring down the guard of even the most suspicious people. Once your selective honesty opens a hole in their armor, you can deceive and manipulate them at will. A timely gift - a Trojan horse - will serve the same purpose. |
| Law 13 | When asking for help, appeal to people's self-interest, never to their mercy or gratitude. | If you need to turn to an ally for help, do not bother to remind him of your past assistance and good deeds. He will find a way to ignore you. Instead, uncover something in your request, or in your alliance with him, that will benefit him, and emphasize it out of all proportion. He will respond enthusiastically when he sees something to be gained for himself. |
| Law 14 | Pose as a friend, work as a spy. | Knowing about your rival is critical. Use spies to gather valuable information that will keep you a step ahead. Better still: play the spy yourself. In polite social encounters, learn to probe. Ask indirect questions to get people to reveal their weaknesses and intentions. There is no occasion that is not an opportunity for artful spying. |
| Law 15 | Crush your enemy totally. | All great leaders since Moses have known that a feared enemy must be crushed completely. (Sometimes they have learned this the hard way.) If one ember is left alight, no matter how dimly it smolders, a fire will eventually break out. More is lost through stopping halfway than through total annihilation: the enemy will recover, and will seek revenge. Crush him, not only in body but in spirit. |
| Law 16 | Use absence to increase respect and honor. | Too much circulation makes the price go down: the more you are seen and heard from, the more common you appear. If you are already established in a group, temporary withdrawal from it will make you more talked about, even more admired. You must learn when to leave. Create value through scarcity. |
| Law 17 | Keep others in suspense: cultivate an air of unpredictability. | Humans are creatures of habit with an insatiable need to see familiarity in other people's actions. Your predictability gives them a sense of control. Turn the tables: be deliberately unpredictable. Behavior that seems to have no consistency or purpose will keep them off balance, and they will wear themselves out trying to explain your moves. Taken to an extreme, this strategy can intimidate and terrorize. |
| Law 18 | Do not build fortresses to protect yourself - isolation is dangerous. | The world is dangerous and enemies are everywhere - everyone has to protect themselves. A fortress seems the safest. But isolation exposes you to more dangers than it protects you from - it cuts you off from valuable information, it makes you conspicuous and an easy target. Better to circulate among people, find allies, mingle. You are shielded from your enemies by the crowd. |
| Law 19 | Know who you're dealing with - do not offend the wrong person. | There are many different kinds of people in the world, and you can never assume that everyone will react to your strategies in the same way. Deceive or outmaneuver some people and they will spend the rest of their lives seeking revenge. They are wolves in lambs' clothing. Choose your victims and opponents carefully, then - never offend or deceive the wrong person. |
| Law 20 | Do not commit to anyone do not commit to anyone. | It is the fool who always rushes to take sides. Do not commit to any side or cause but yourself. By maintaining your independence, you become the master of others - playing people against one another, making them pursue you. |
| Law 21 | Play a sucker to catch a sucker - seem dumber than your mark. | No one likes feeling stupider than the next person. The trick, then, is to make your victims feel smart - and not just smart, but smarter than you are. Once convinced of this, they will never suspect that you may have ulterior motives. |
| Law 22 | Use the surrender tactic: transform weakness into power. | When you are weaker, never fight for honor's sake; choose surrender instead. Surrender gives you time to recover, time to torment and irritate your conqueror, time to wait for his power to wane. Do not give him the satisfaction of fighting and defeating you - surrender first. By turning the other cheek you infuriate and unsettle him. Make surrender a tool of power. |
| Law 23 | Concentrate your forces. | Conserve your forces and energies by keeping them concentrated at their strongest point. You gain more by finding a rich mine and mining it deeper, than by flitting from one shallow mine to another - intensity defeats extensity every time. When looking for sources of power to elevate you, find the one key patron, the fat cow who will give you milk for a long time to come. |
| Law 24 | Play the perfect courtier. | The perfect courtier thrives in a world where everything revolves around power and political dexterity. He has mastered the art of indirection; he flatters, yields to superiors, and asserts power over others in the most oblique and graceful manner. Learn and apply the laws of courtiership and there will be no limit to how far you can rise in the court. |
| Law 25 | Re-create yourself. | Do not accept the roles that society foists on you. Re-create yourself by forging a new identity, one that commands attention and never bores the audience. Be the master of your own image rather than letting others define it for you. Incorporate dramatic devices into your public gestures and actions - your power will be enhanced and your character will seem larger than life. |
| Law 26 | Keep your hands clean. | You must seem a paragon of civility and efficiency: your hands are never soiled by mistakes and nasty deeds. Maintain such a spotless appearance by using others as unwitting pawns and screens to disguise your involvement. |
| Law 27 | Play on people's need to believe to create a cultlike following. | People have an overwhelming desire to believe in something. Become the focal point of such desire by offering them a cause, a new faith to follow. Keep your words vague but full of promise; emphasize enthusiasm over rationality and clear thinking. Give your new disciples rituals to perform, ask them to make sacrifices on your behalf. In the absence of organized religion and grand causes, your new belief system will bring you untold power. |
| Law 28 | Enter action with boldness. | If you are unsure of a course of action, do not attempt it. Your doubts and hesitations will infect your execution. Timidity is dangerous: better to enter with boldness. Any mistakes you commit through audacity are easily corrected with more audacity. Everyone admires the bold; no one honors the timid. |
| Law 29 | Plan all the way to the end. | The ending is everything. Plan all the way to it, taking into account all the possible consequences, obstacles, and twists of fortune that might reverse your hard work and give the glory to others. By planning to the end you will not be overwhelmed by circumstances and you will know when to stop. Gently guide fortune and help determine the future by thinking far ahead. |
| Law 30 | Make your accomplishments seem effortless. | Your actions must seem natural and executed with ease. All the toil and practice that go into them, and also all the clever tricks, must be concealed. When you act, act effortlessly, as if you could do much more. Avoid the temptation of revealing how hard you work - it only raises questions. Teach no one your tricks or they will be used against you. |
| Law 31 | Control the options: get others to play with the cards you deal. | The best deceptions are the ones that seem to give the other person a choice: your victims feel they are in control, but are actually your puppets. Give people options that come out in your favor whichever one they choose. Force them to make choices between the lesser of two evils, both of which serve your purpose. Put them on the horns of a dilemma: they are gored wherever they turn. |
| Law 32 | Play to people's fantasies play to people's fantasies. | The truth is often avoided because it is ugly and unpleasant. Never appeal to truth and reality unless you are prepared for the anger that comes from disenchantment. Life is so harsh and distressing, that people who can manufacture romance or conjure up fantasy are like oases in the desert: everyone flocks to them. There is great power in tapping into the fantasies of the masses. |
| Law 33 | Discover each man's thumbscrew. | Everyone has a weakness, a gap in the castle wall. That weakness is usually an insecurity, an uncontrollable emotion or need; it can also be a small secret pleasure. Either way, once found, it is a thumbscrew you can turn to your advantage. |
| Law 34 | Be royal in your own fashion: act like a king to be treated like one. | The way you carry yourself will often determine how you are treated: in the long run, appearing vulgar or common will make people disrespect you. For a king respects himself, and inspires the same sentiment in others. By acting regally and confident of your powers, you make yourself seem destined to wear a crown. |
| Law 35 | Master the art of timing. | Never seem to be in a hurry - hurrying betrays a lack of control over yourself, and over time. Always seem patient, as if you know that everything will come to you eventually. Become a detective of the right moment; sniff out the spirit of the times, the trends that will carry you to power. Learn to stand back when the time is not yet ripe, and to strike fiercely when it has reached fruition. |
| Law 36 | Disdain things you cannot have: ignoring them is the best revenge. | By acknowledging a petty problem you give it existence and credibility. The more attention you pay an enemy, the stronger you make him; and a small mistake is often made worse and more visible when you try to fix it. It is sometimes best to leave things alone. If there is something you want but cannot have, show contempt for it. The less interest you reveal, the more superior you seem. |
| Law 37 | Create compelling spectacles. | Striking imagery and grand symbolic gestures create the aura of power - everyone responds to them. Stage spectacles for those around you, then, full of arresting visuals and radiant symbols that heighten your presence. Dazzled by appearances, no one will notice what you are really doing. |
| Law 38 | Think as you like but behave like others. | If you make a show of going against the times, flaunting your unconventional ideas and unorthodox ways, people will think that you only want attention and that you look down upon them. They will find a way to punish you for making them feel inferior. It is far safer to blend in and nurture the common touch. Share your originality only with tolerant friends and those who are sure to appreciate your uniqueness. |
| Law 39 | Stir up waters to catch fish. | Anger and emotion are strategically counterproductive. You must always stay calm and objective. But if you can make your enemies angry while staying calm yourself, you gain a decided advantage. Put your enemies off-balance: find the chink in their vanity through which you can rattle them and you hold the strings. |
| Law 40 | Despise the free lunch. | What is offered for free is dangerous - it usually involves either a trick or a hidden obligation. What has worth is worth paying for. By paying your own way you stay clear of gratitude, guilt, and deceit. It is also often wise to pay the full price - there is no cutting corners with excellence. Be lavish with your money and keep it circulating, for generosity is a sign and a magnet for power. |
| Law 41 | Avoid stepping into a great man's shoes. | What happens first always appears better and more original than what comes after. If you succeed a great man or have a famous parent, you will have to accomplish double their achievements to outshine them. Do not get lost in their shadow, or stuck in a past not of your own making: establish your own name and identity by changing course. Slay the overbearing father, disparage his legacy, and gain power by shining in your own way. |
| Law 42 | Strike the shepherd and the sheep will scatter. | Trouble can often be traced to a single strong individual - the stirrer, the arrogant underling, the poisoner of good will. If you allow such people room to operate, others will succumb to their influence. Do not wait for the troubles they cause to multiply, do not try to negotiate with them - they are irredeemable. Neutralize their influence by isolating or banishing them. Strike at the source of the trouble and the sheep will scatter. |
| Law 43 | Work on the hearts and minds of others. | Coercion creates a reaction that will eventually work against you. You must seduce others intowanting to move in your direction. A person you have seduced becomes your loyal pawn. And the way to seduce others is to operate on their individual psychologies and weaknesses. Soften up the resistant by working on their emotions, playing on what they hold dear and what they fear. Ignore the hearts and minds of others and they will grow to hate you. |
| Law 44 | Disarm and infuriate with the mirror effect. | The mirror reflects reality, but it is also the perfect tool for deception: when you mirror your enemies, doing exactly as they do, they cannot figure out your strategy. The Mirror Effect mocks and humiliates them, making them overreact. By holding up a mirror to their psyches, you seduce them with the illusion that you share their values; by holding up a mirror to their actions, you teach them a lesson. Few can resist the power of the Mirror Effect. |
| Law 45 | Preach the need for change, but never reform too much at once. | Everyone understands the need for change in the abstract, but on the day-to-day level people are creatures of habit. Too much innovation is traumatic, and will lead to revolt. If you are new to a position of power, or an outsider trying to build a power base, make a show of respecting the old way of doing things. If change is necessary, make it feel like a gentle improvement on the past. |
| Law 46 | Never appear too perfect. | Appearing better than others is always dangerous, but most dangerous of all is to appear to have no faults or weaknesses. Envy creates silent enemies. It is smart to occasionally display defects, and admit to harmless vices, in order to deflect envy and appear more human and approachable. Only gods and the dead can seem perfect with impunity. |
| Law 47 | Do not go past the mark you aimed for; in victory, learn when to stop. | The moment of victory is often the moment of greatest peril. In the heat of victory, arrogance and overconfidence can push you past the goal you had aimed for, and by going too far, you make more enemies than you defeat. Do not allow success to go to your head. There is no substitute for strategy and careful planning. Set a goal, and when you reach it, stop. |
| Law 48 | Assume formlessness. | By taking a shape, by having a visible plan, you open yourself to attack. Instead of taking a form for your enemy to grasp, keep yourself adaptable and on the move. Accept the fact that nothing is certain and no law is fixed. The best way to protect yourself is to be as fluid and formless as water; never bet on stability or lasting order. Everything changes. |